One of the most widely used cloud-native services are cloud-orchestrated containers. Kubernetes, where public cloud services are one of the most used for this type of workload. In fact, in one of the 2020 cncf.io surveys, it shows us that about 60% of users / companies use cloud-native storage for their containers directly from Google (81%), AWS (80%) and Azure ( 74%), surely these percentages have changed over the years. That is why in this post we will review how to protect all containers in AWS EKS.
Initial Steps
Initially, since I mentioned the cncf.io report, you can check it out here:
https://www.cncf.io/wp-content/uploads/2020/12/CNCF_Survey_Report_2020.pdf
As always we must review the official documentation of Kasten:
https://docs.kasten.io/latest/install/aws/aws.html
Here we will see the recommended way of installation, there is another, but we must always try to approach good practices.
Installation Kasten with IAM Role
The recommended way is to use the integration with an IAM role associated with a service account, in this case, k10-k10, therefore we will start by creating the IAM policies to assign the permissions according to the official configuration of Kasten:
- https://docs.kasten.io/latest/install/aws/using_aws_iam_roles.html#using-aws-iam-roles
- https://docs.kasten.io/latest/install/aws/aws_permissions.html
The first link tells us the necessary permissions to take snapshots, restore and migrate between different clusters. In the second link we see all the permissions for each service that access is needed according to what you need to protect. In this case we will see 3 IAM policies to create and have a granularity of permissions to the service account.
We will generate 3 policies, associated to the json that shows us the documentation of KastenFor example, to make the AWS EBS policy we must click on “Create Policy”, click on “JSON” and paste the content:
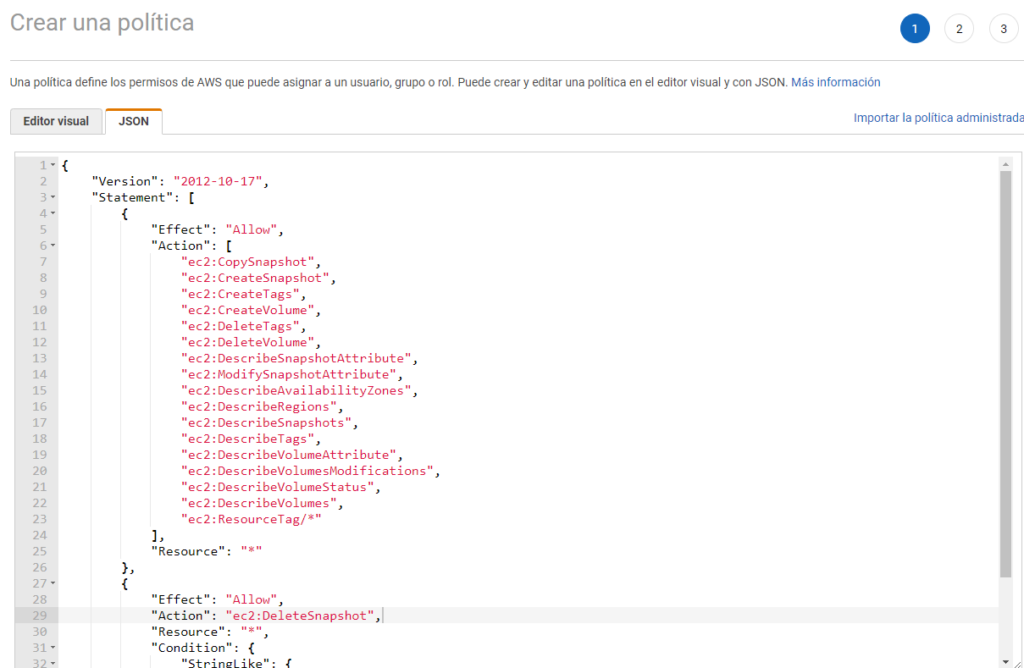
Then, click on next, to apply tags and then as a last step we will enter the name of the policy:
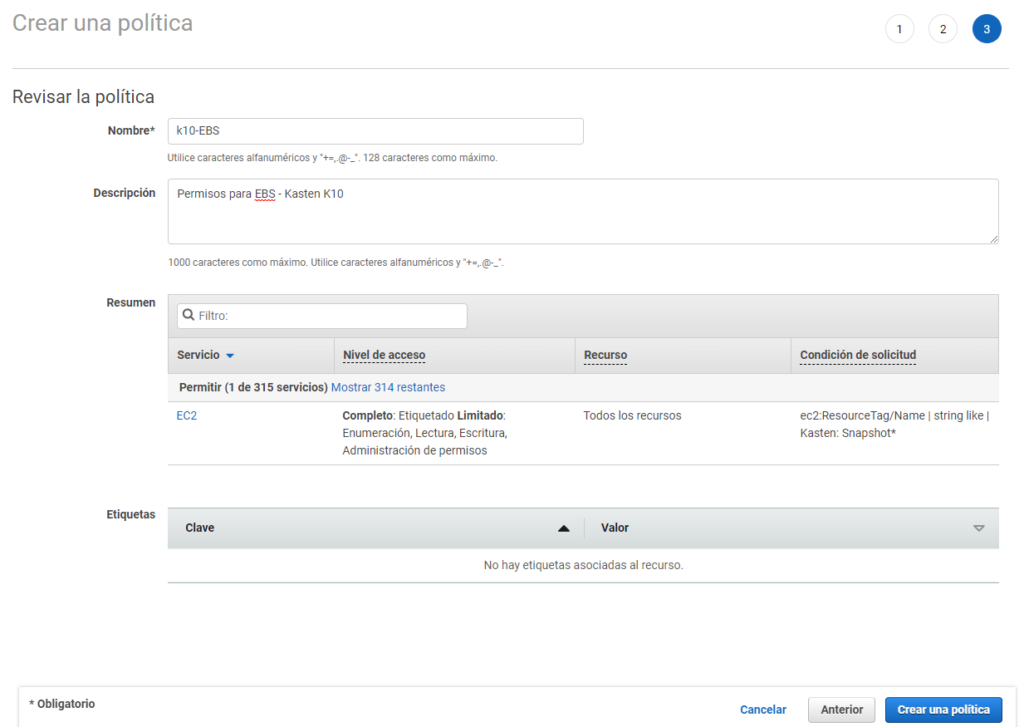
**Important: The necessary policies must be created, therefore, this step must be repeated, with the policies for the necessary services from the second previous link**
Enable OIDC on EKS
We must use Cloudshell or a local configuration of aws cli, configuring the Authentikation as an administrator user for the management of the following commands.
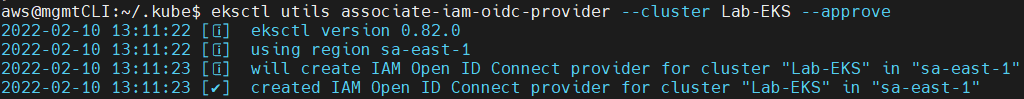
To have a correct Authentikation, we can configure OIDC in our cluster EKS with the following command (you must enter the name of your cluster):
eksctl utils associate-iam-oidc-provider --cluster NombreCluster --approve
As stated in the documentation:
It should be considered that the name of the service account that we will create must be "k10-k10”, the namespace “kasten-io” and also add the ARN of the policies that we generate, to obtain the ARN of the policies, you must enter IAM and click on the name of the policy to see the ARN, we copy each of the ARN of the created policies previously:
Now we will create the namespace “kasten-io”
kubectl create ns kasten-io

And then we generate the service account with the following command:
eksctl create iamserviceaccount \
--name k10-k10 \
--namespace kasten-io \
--cluster Lab-EKS \
--attach-policy-arn arn:aws:iam::123456789000:policy/k10-EBS \
--attach-policy-arn arn:aws:iam::123456789000:policy/k10-RDS \
--attach-policy-arn arn:aws:iam::123456789000:policy/k10-S3 \
--approve \
--override-existing-serviceaccounts
**remember to enter the name of the cluster EKS and the RNA of each policy**
After this we will see in IAM, a new Role:
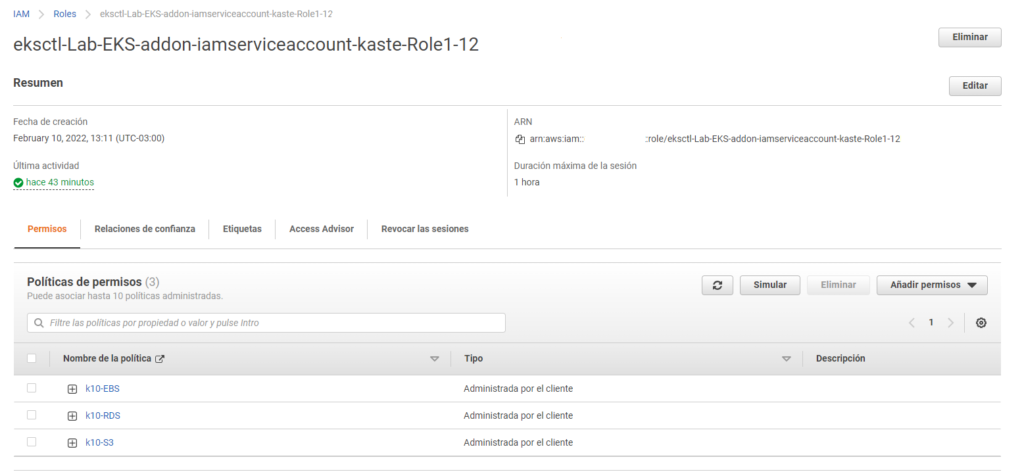
As seen in the previous image, the policies are associated with this new role generated and associated with the service account. We will copy the ARN of the new role and proceed to the installation of Kasten K10
Installation Kasten K10 AWS EKS
As we have seen several times in this blog, we must have "helm" configured with its respective chart, you can see it here:
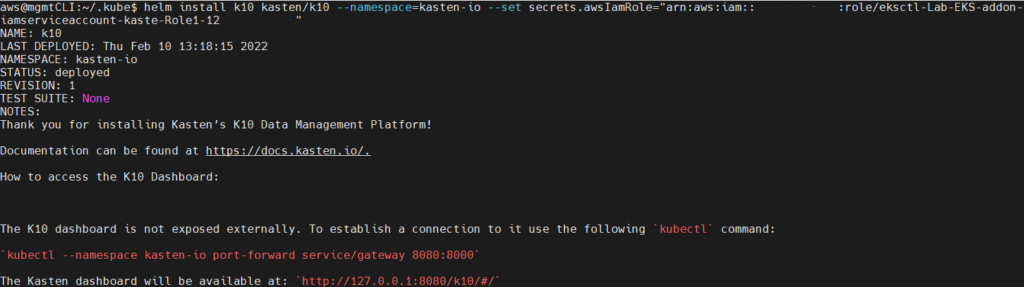
And now we will install Kasten K10 with the following command:
helm install k10 kasten/k10 --namespace=kasten-io --set secrets.awsIamRole="arn:aws:iam::123456789000:role/eksctl-Lab-EKS-addon-iamserviceaccount-kaste-Role1-12FASDASDCKA"
*Remember that you must enter the ARN of the previously created Role*
** In case you get an error claiming the existence of a service account, just delete and re-create the namespace kasten-io**
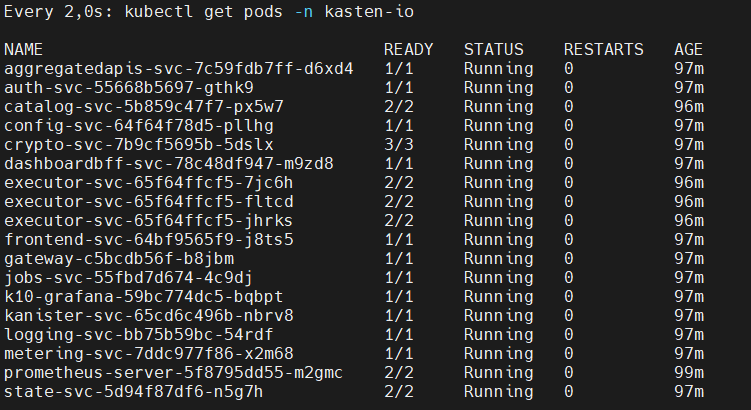
We hope that the pods of “kasten-io” remain in the “running” state by checking them with the following command:
watch kubectl get pods -n kasten-io
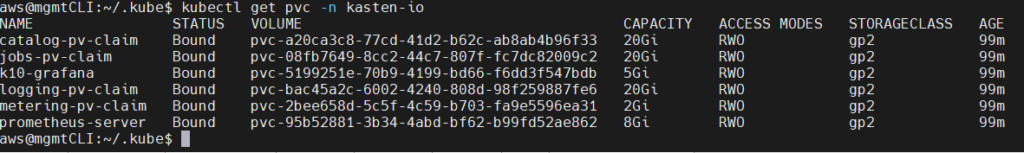
If you want to see the disks that were created automatically with the installation of Kasten K10:
kubectl get pvc -n kasten-io
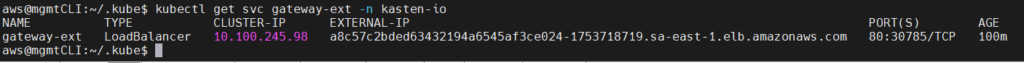
Finally we need access to the console Kasten K10, we just have to execute the following command:
helm upgrade k10 kasten/k10 --namespace=kasten-io \
--reuse-values \
--set externalGateway.create=true \
--set auth.tokenAuth.enabled=true
Which will create a "Load Balancer" service and assign an AWS dns address:
kubectl get svc gateway-ext -n kasten-io
We only have to enter the url, in this case:
http://a8c57c2bded63432194a6545af3ce024-1753718719.sa-east-1.elb.amazonaws.com/k10/#/
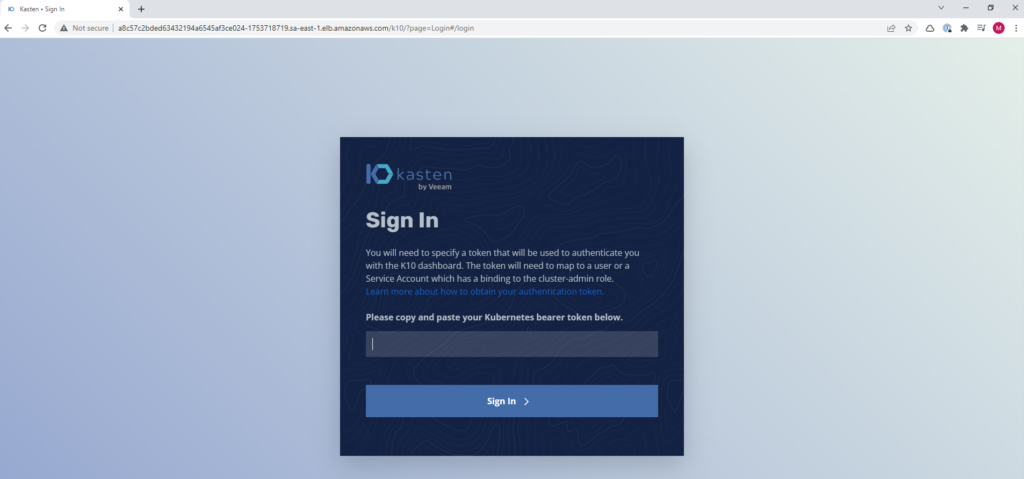
and we will proceed to Authentikate as seen in the official documentation:
https://docs.kasten.io/latest/access/Authentikation.html#obtaining-tokens
So far you can use Kasten K10 to back up your loads on AWS EKS : )
integrate with K10 Multi-Cluster Manager AWS EKS
We have already seen how to install K10 Multi-Cluster Manager, if you haven't checked it out yet:
or install K10 Multi-Cluster Manager without Keycloak:
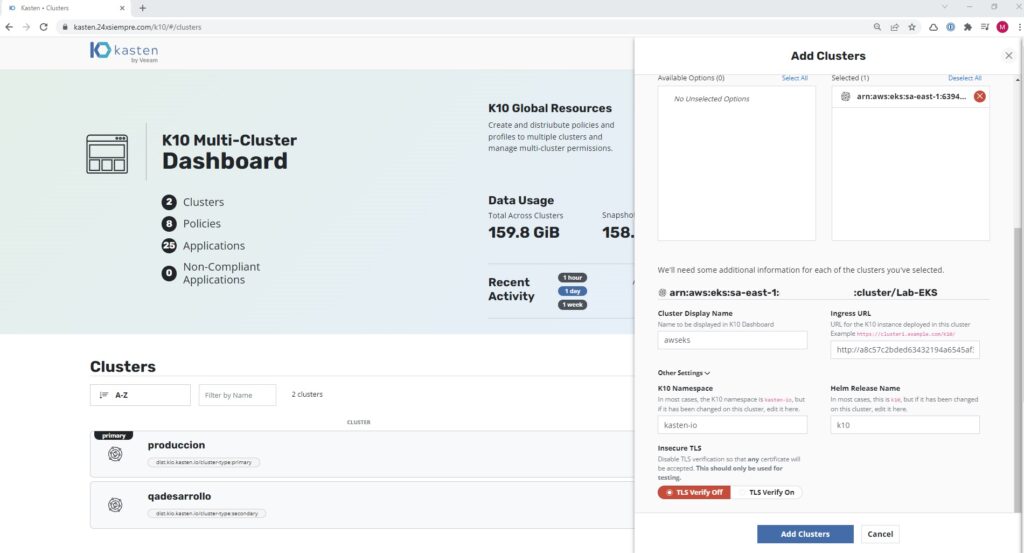
Now, we have to configure the kubeconfig file in our Multi-Cluster Manager interface, we will try to add the cluster through the web interface, by clicking on “Add Clusters” and we will paste the content of the kubeconfig file of our AWS cluster EKS and it will show us the following:
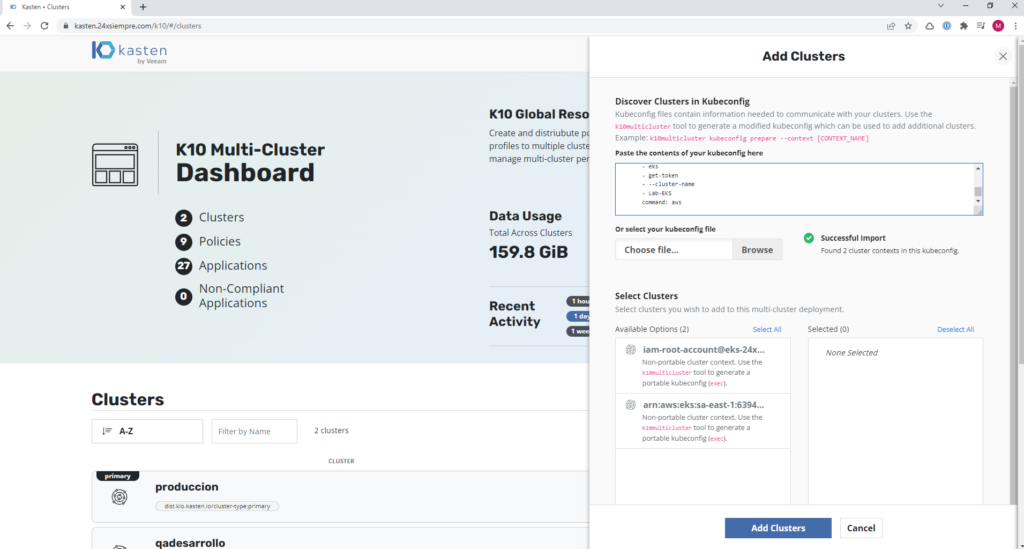
As we can see, the cluster cannot be selected, since K10MultiCluster needs a previous step to prepare the kubeconfig file correctly, for this we will perform the following command to identify the context of kubernetes used:
kubectl config get-contexts
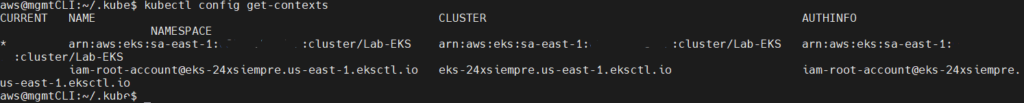
We copy the name of the context and then we execute the command:
k10multicluster kubeconfig prepare --context arn:aws:eks:sa-east-1:12345678900:cluster/Lab-EKS
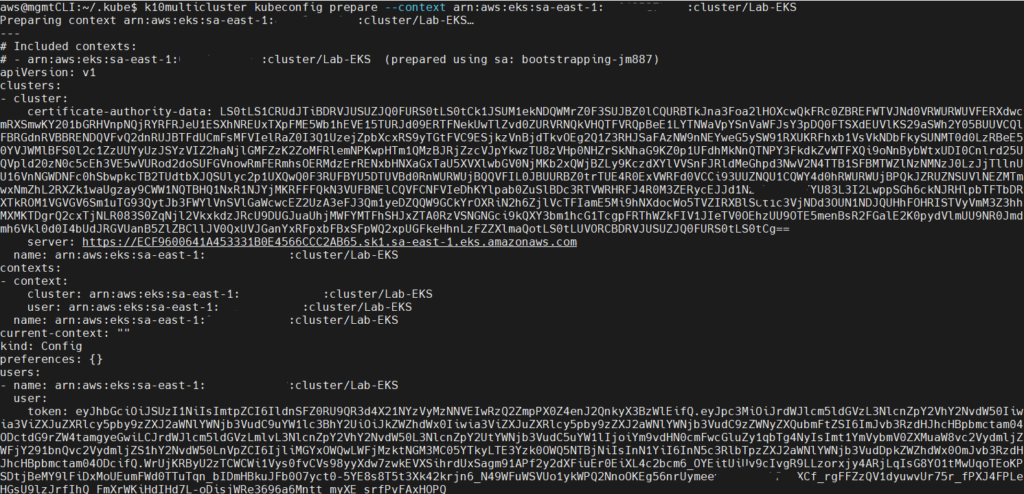
We copy the content after “—” and paste it again in K10 Multi-Cluster Manager in “Add Clusters” and we will see that the options are now enabledones to add the AWS cluster EKS:
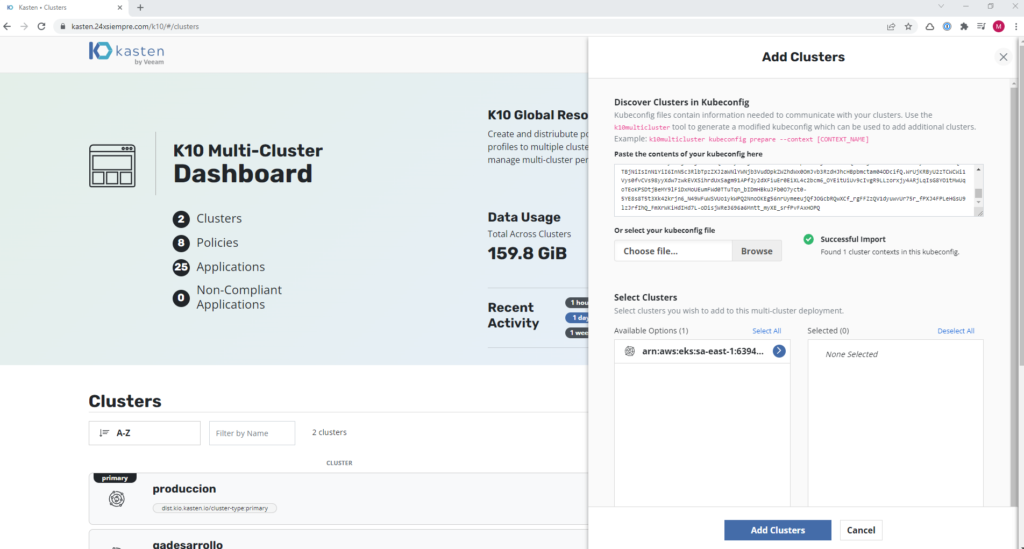
We select the cluster and pass it to the right, to then enter the "Cluster Display Name", the "Ingress URL" which is the URL that was assigned to us in the services of kasten-io, always adding as indicated by the interface, namespace “kasten-io”, helm release name “k10” and disable TLS, since we are adding it without TLS, in case you configure access with a certificate, enable it, then click on “Add Clusters”:
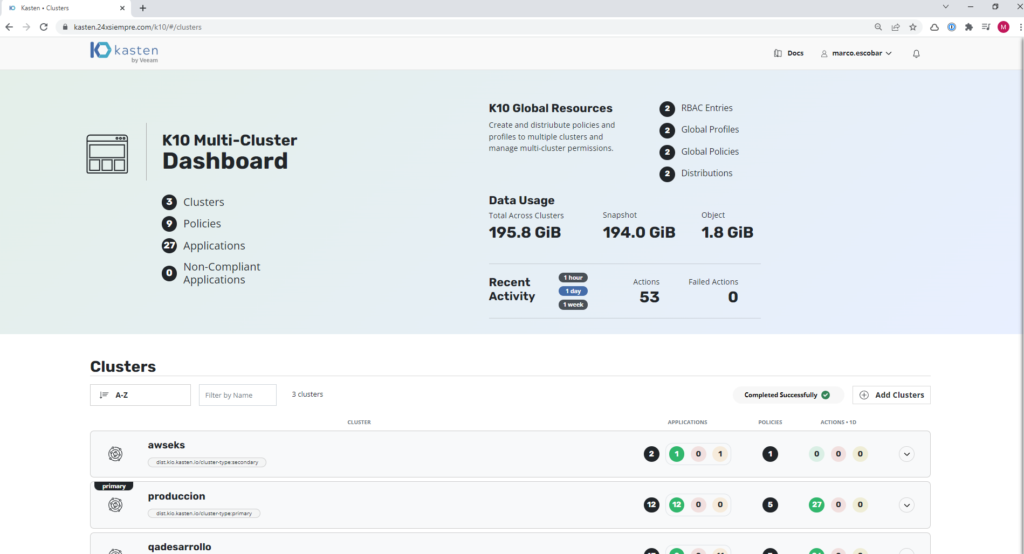
And we will have the AWS cluster EKS at our K10 Multi-Cluster Manager configured to apply the necessary policies.
Add S3 Bucket with IAM Role
As previously we configured all the permissions associated with a service account of kasten k10 and the policies associated with the role created, when we configure a "Location Profile" we can use the same IAM Role for Authentikation by selecting:
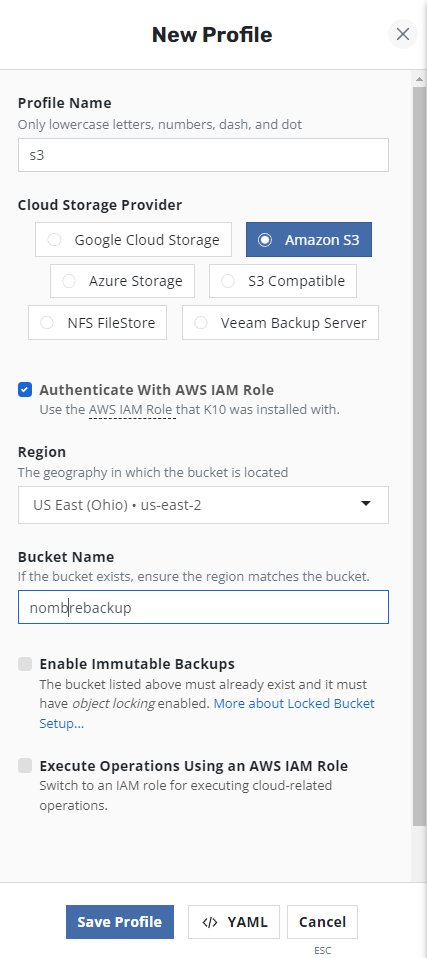
We enter the Region, Bucket Name and save the profile, of course if the bucket has immutability enabled you can also use it.
Recommendations
I always recommend things at the security level, always only allow the IP's authorized to access the services of kasten, through firewall rules to preserve privacy, on the other hand, if it is necessary to generate more permissions to the role, you should only generate the necessary policy, such as to support with the necessary permissions of RDS and associate it to the generated role.
