One of the characteristics of Kasten K10 most used, is the integration with centralized Authentikation and identity systems, through different protocols, for the management of access to the different clusters of kubernetes using RBAC by means of K10 and/or for the access of K10 Multi-Cluster in environments with multiple clusters of kubernetes. In this post, we will review the easy setup of Authentik and integration with Kasten K10.
Initial Steps
In this guide we will see how easy it is to configure Authentik with Kasten K10, using the default variables of the installation of Kasten K10 in relation to the groups used for role-based access management.
As usual, we will review the official documentation of the resources that we will use.
Authentik https://goauthentik.io/
Kasten K10 https://docs.kasten.io/latest/
RBAC Kasten K10 https://docs.kasten.io/latest/access/rbac.html
RBAC Kasten K10 K10 Multi-Cluster Manager https://docs.kasten.io/latest/multicluster/rbac.html
Authentik
What is Authentik? As we have already seen in this blog, there are multiple solutions Open Source for identity management, roles, integration with kubernetes and/or single sign on (SSO), for example, we have previously reviewed Keycloak, in this post we will review Authentik, which is another platform widely used in different companies for managing single access, as well as access protection by Authentikation of applications via different protocols or through proxy.
Kasten K10, supports multiple Authentikation protocols, of course, we will use OpenID which allows us to easily Authentikate each other Kasten and Kasten K10 for centralized user management. Authentik installation is very simple and has different ways of installation, in my case, I installed it on kubernetes with helm, you can check the options in:
https://goauthentik.io/docs/installation
Configuration Requirements Authentik
After installation, Authentik asks to create the credentials of the initial user "akadmin", to then log in Authentik, we enter the “Administrator Interface”:
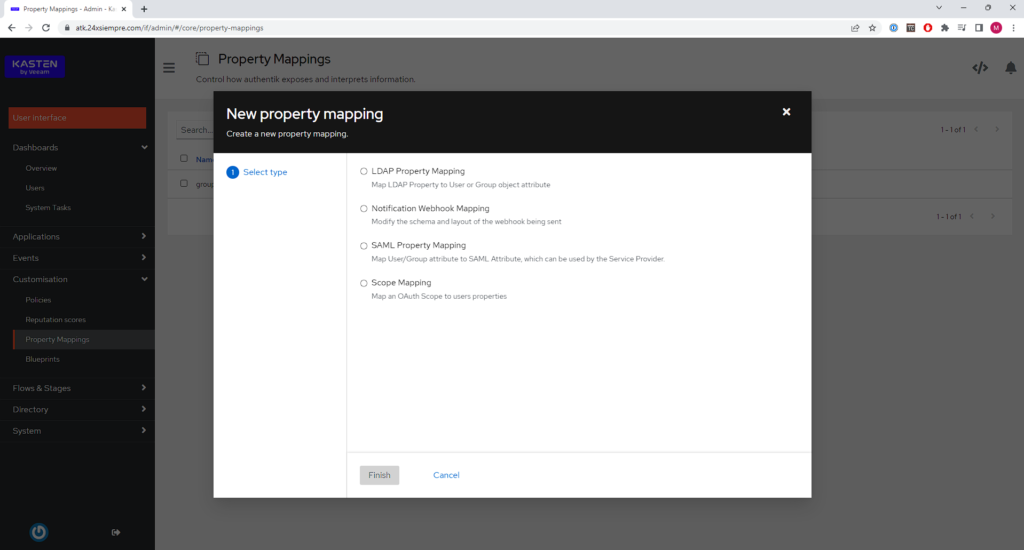
Now we will enter from the menu in “Customisation”, “Property Mappings” and finally click on “Create”:
At this stage we will select “Scope Mapping” click on “Next” and add the scope “groups” and the expression as shown in the following image:
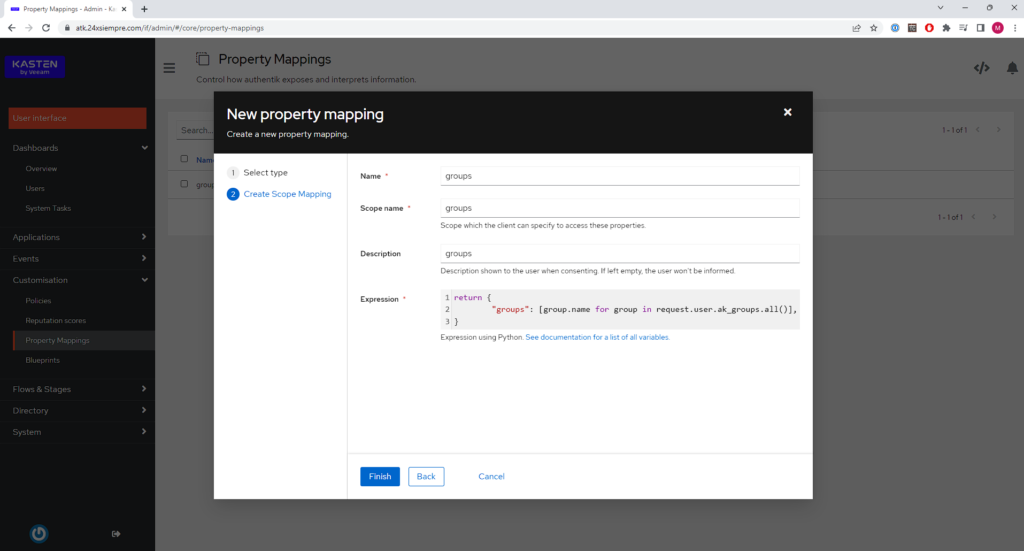
return {
"groups": [group.name for group in request.user.ak_groups.all()],
}
With the previous configuration, we will be able to use or map the groups of Kasten K10 to assign access to the console K10, that is, we will be able to create users in Authentik, create and assign groups of K10 to the users created and access, therefore, we will validate that it works correctly by clicking the test icon, selecting a user and pressing “Test”
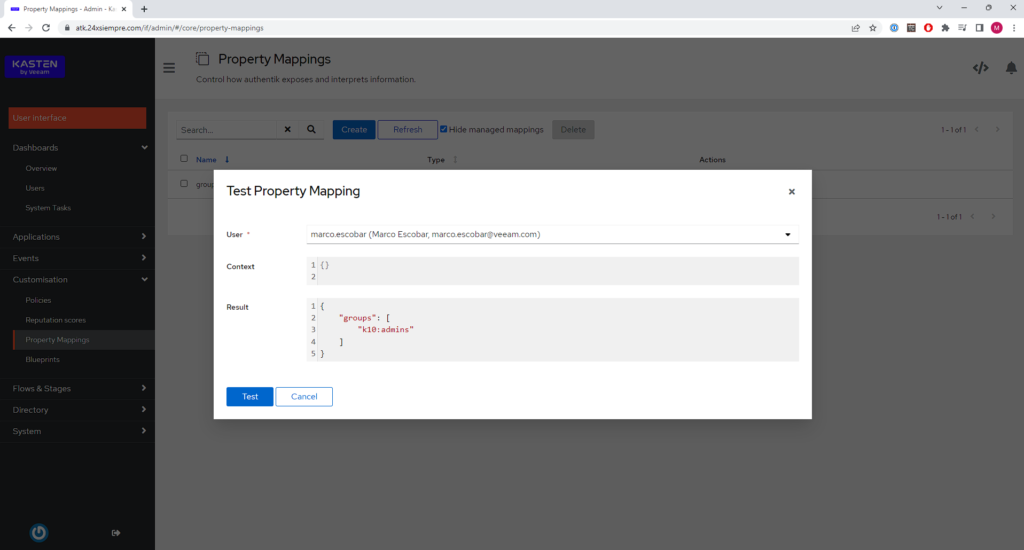
Bringing the groups to which the user belongs means that the "Scope" is working correctly. If the user does not have any group assigned, it will not show anything, therefore, now we will proceed to create the first administration group for Kasten K10 en Authentik.
Creation of Users and Groups in Authentik
To integrate Authentik with Kasten K10, we need of course to create users and groups that are related to K10, in this case, we will start by creating the group “k10:admins”, which allows you to have administrator access to the console K10 o Multi-Cluster Manager, we will enter “Directory” then “Groups” and click on “Create”:
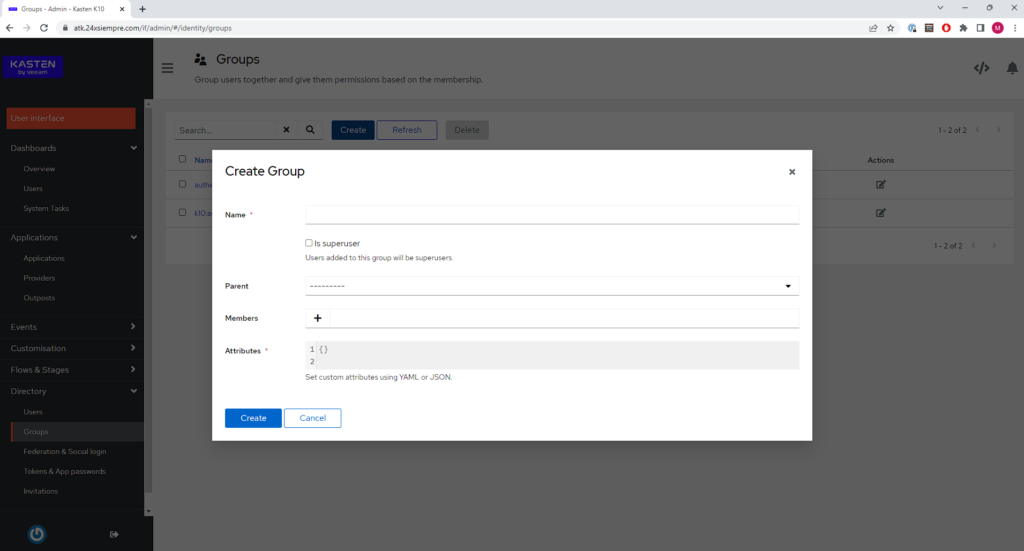
Enter the name of the group "k10:admins" and click “Create”:
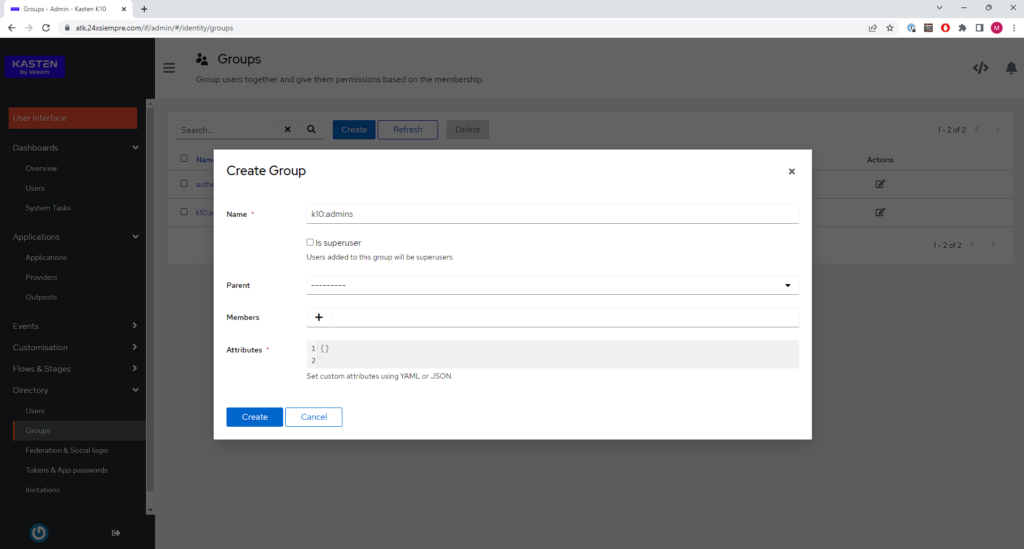
Now we will create a user and in the same creation we will add it to the same group that we just created. Therefore, now we will enter “Directory” and then “Users”, we enter the “Username”, “Name”, “Email”, and by clicking on “+” we add it to the group that we created previously.
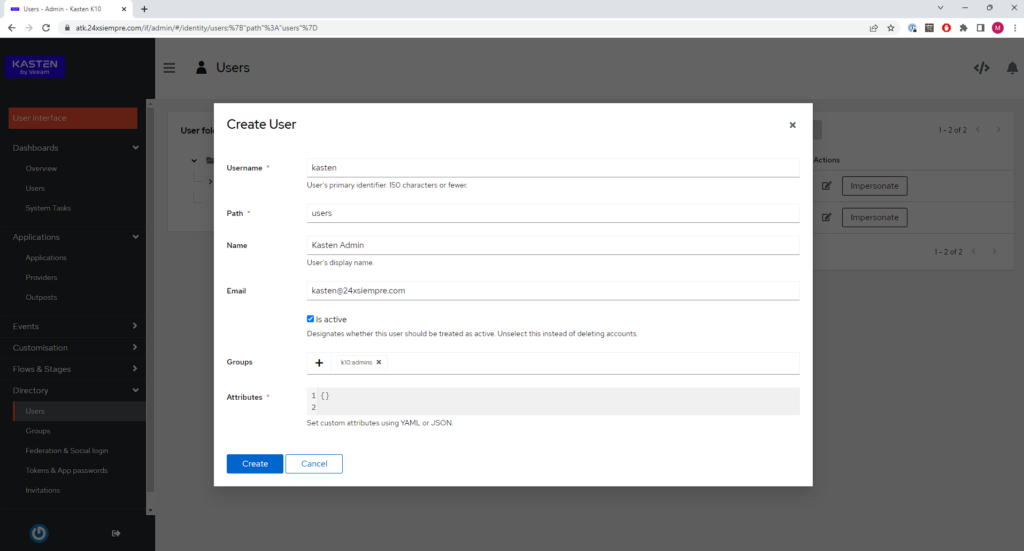
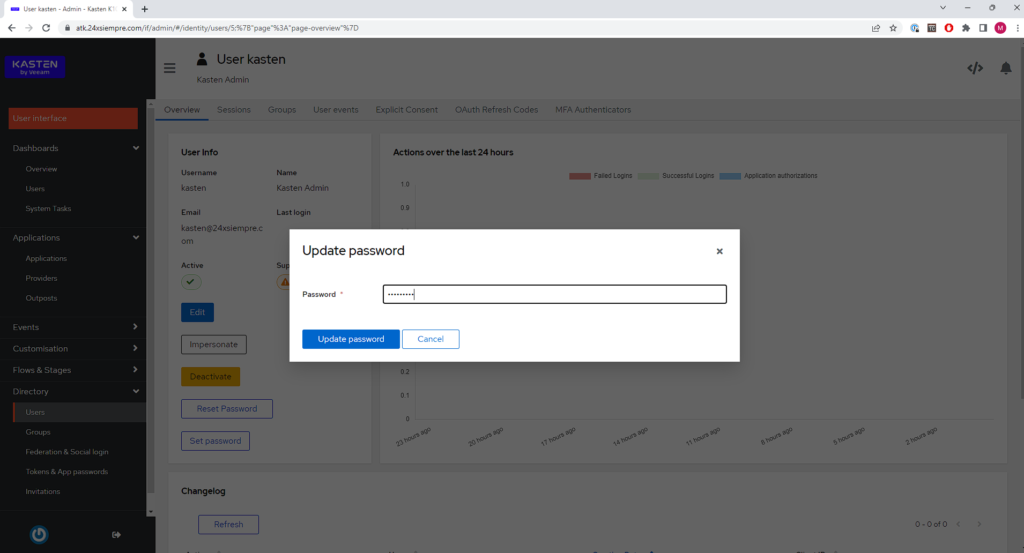
Next, we select the newly created user and click on “Set Password” and enter the desired password:
OpenID creation in Authentik
now for what Authentik, can be integrated with Kasten K10, we need to enable and configure the OpenID protocol, we enter “Applications”, then “Providers” and click on “Create”
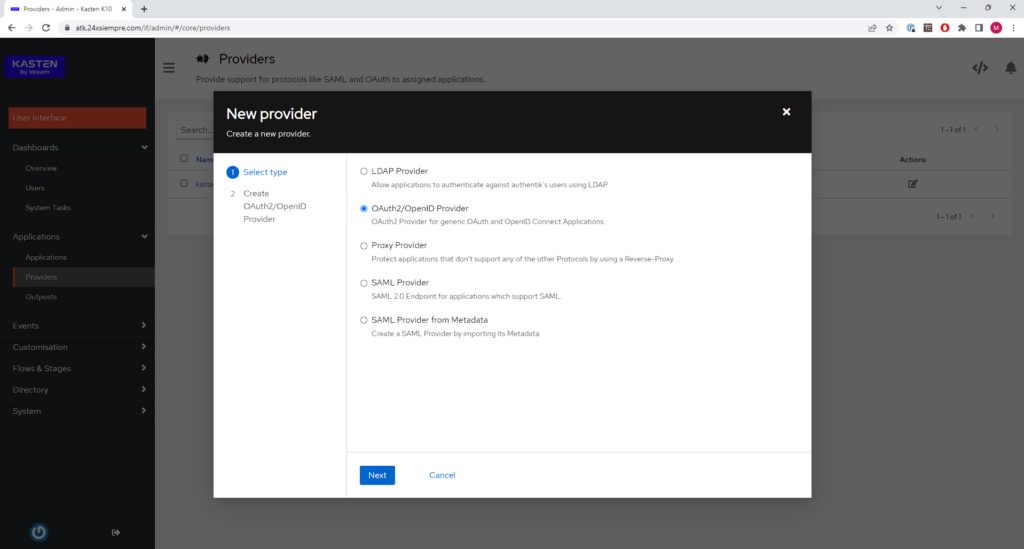
At this stage we must select “OAuth2/OpenID Provider” and click “Next” to move on to the most important stage, now we enter the name and leave the default “Authorization Flow”:
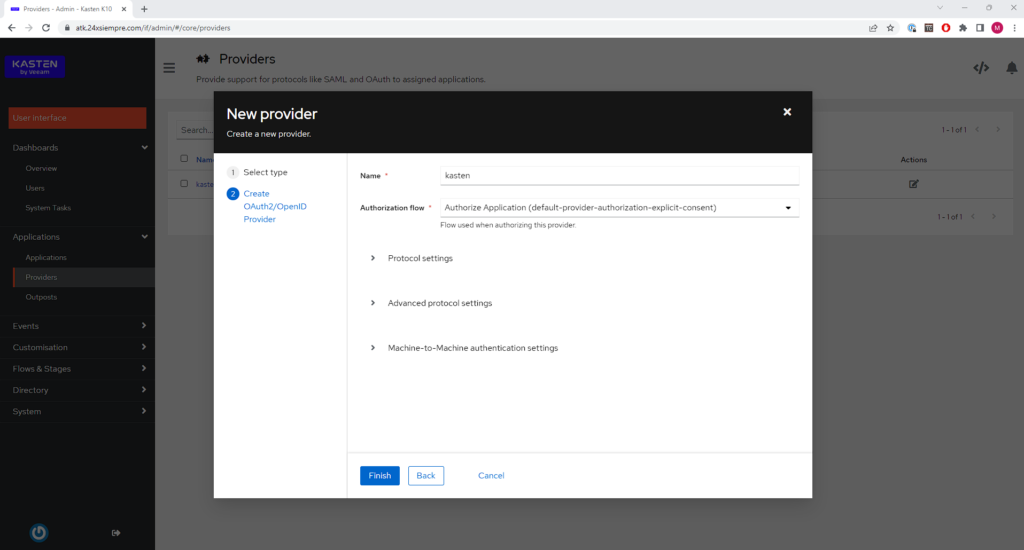
Now in “Protocol Settings”
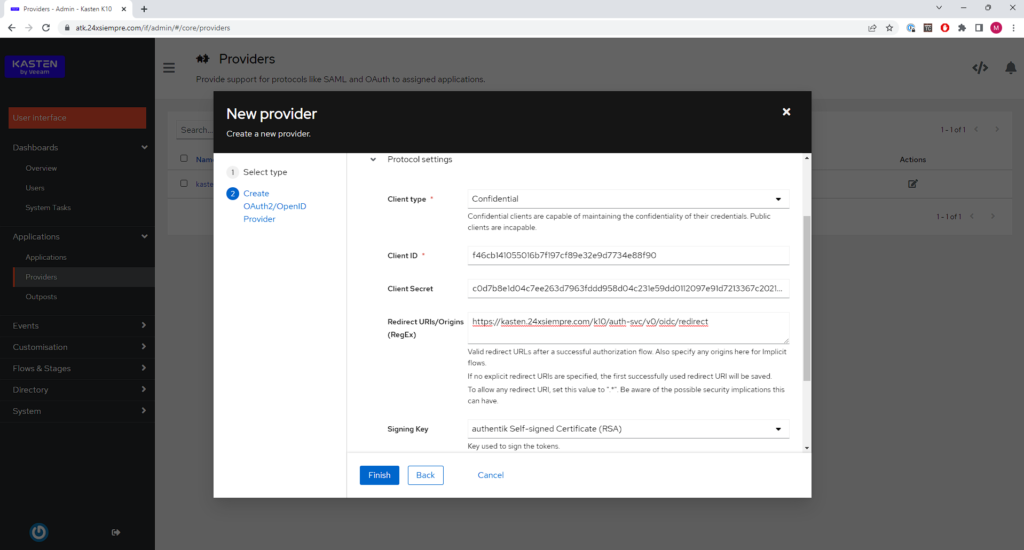
Where:
- ClientType: Confidential
- Customer ID: Automatically generated (copy to a notepad)
- Client Secrets: Automatically generated (copy to a notepad)
- Redirect Uri/Origins: https://kast24xsiempre.com/en/k10/auth-svc/v0/oidc/redirect
- Signing Key: Authentik self-signed
Then in “Advanced protocol Settings”, make sure that the Scopes “groups” is selected:
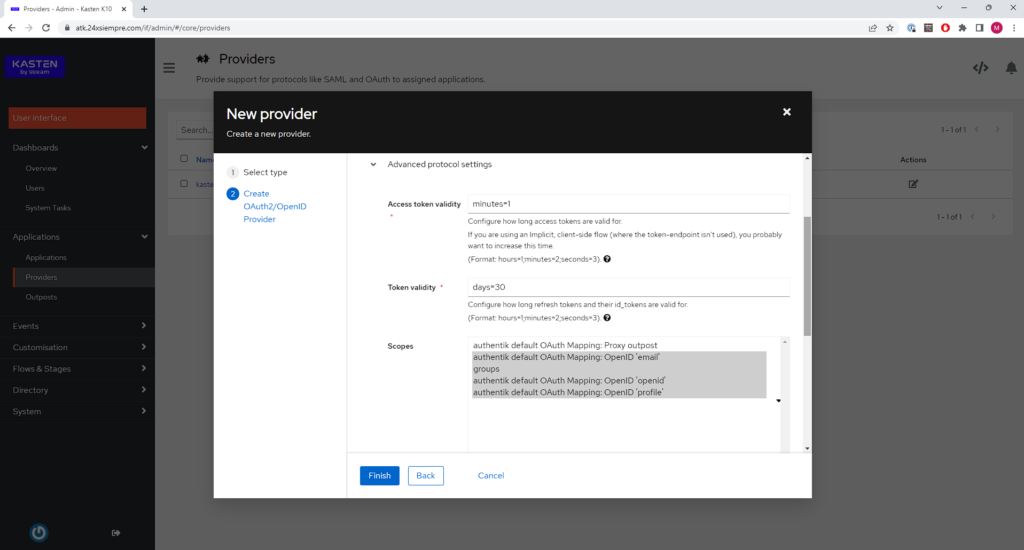
And finally click on “Finish”.
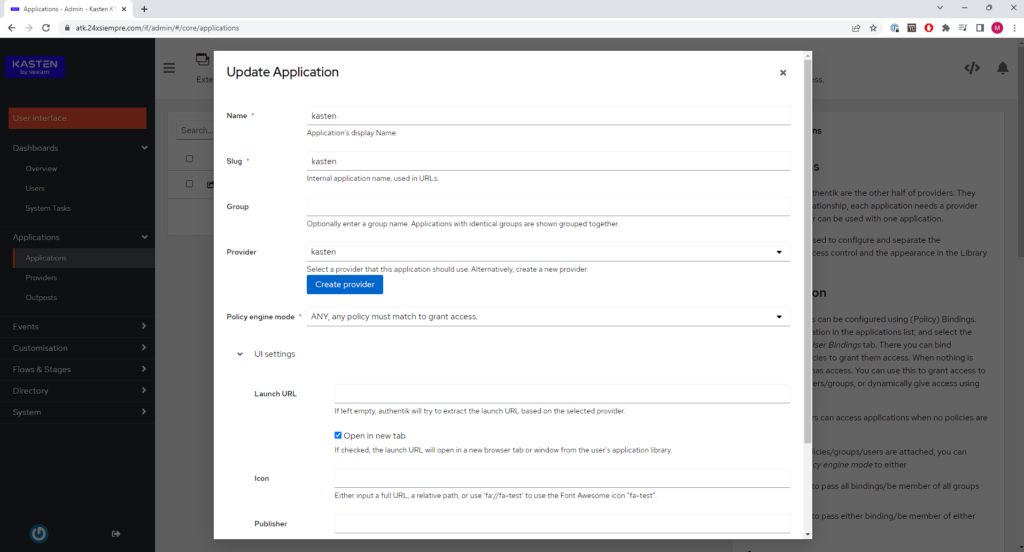
Creation of Application in Authentik
For Authentik provide the service, an application is generated, entering "Applications" and again in "Applications" to click on "Create", we enter the "Name", the "Slug" and in "Provider" we select the OpenID provider that we create above, ending with clicking “Create”
Setting Kasten K10
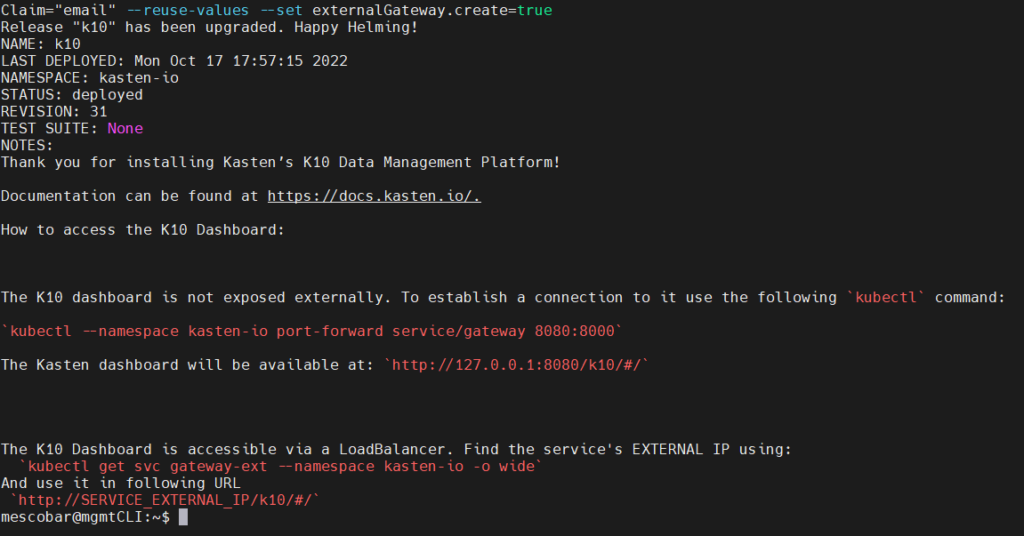
As we saw earlier in the documentation, https://docs.kasten.io/latest/access/rbac.html#k10-admin-binding, we know we have the group “k10:admins” and we already have it mapped with our installation of Authentik, next we will see the command to execute in our installation of Kasten K10 or in the primary cluster of K10 Multi Cluster Manager:
helm upgrade k10 kasten/k10 --namespace=kasten-io --set auth.oidcAuth.enabled=true --set auth.oidcAuth.providerURL="https://atk.24xsiempre.com/application/o/kasten/" --set auth.oidcAuth.redirectURL="https://kast24xsiempre.com/en/" --set auth.oidcAuth.scopes="groups profile email" --set auth.oidcAuth.groupClaim="groups" --set auth.oidcAuth.prompt="login" --set auth.oidcAuth.clientID="SuperDuperClientID" --set auth.oidcAuth.clientSecret="SuperDuperClientSecret" --set auth.oidcAuth.usernameClaim="email" --reuse-values --set externalGateway.create=true
Now we will see what each of these variables means:
- --set auth.oidcAuth.enabled=true / We enable OpenID Authentikation
- –set auth.oidcAuth.providerURL="https://atk.24xsiempre.com/application/o/kasten" / Url to Authenticate
- –set auth.oidcAuth.redirectURL="https://kast24xsiempre.com/en/" / application url K10
- --set auth.oidcAuth.scopes=”groups profile email” / Client Scopes to validate
- --set auth.oidcAuth.groupClaim=”groups” / Client Scope Group Name
- --set auth.oidcAuth.prompt=”login” / Login Message
- --set auth.oidcAuth.clientID=”SuperDuperClientID” / Client ID
- --set auth.oidcAuth.clientSecret=”SuperDuperClientSecret” /Client secret
- --set auth.oidcAuth.usernameClaim=”email” / In case of email Authentikation
- --reuse-values / Reuse values already configured
- --set externalGateway.create=true / Reconfigure gateway service in K10 for remote access
Console Access Kasten K10
By entering the url address https://kast24xsiempre.com/en/k10/#/ will be redirected to the login of Authentik:
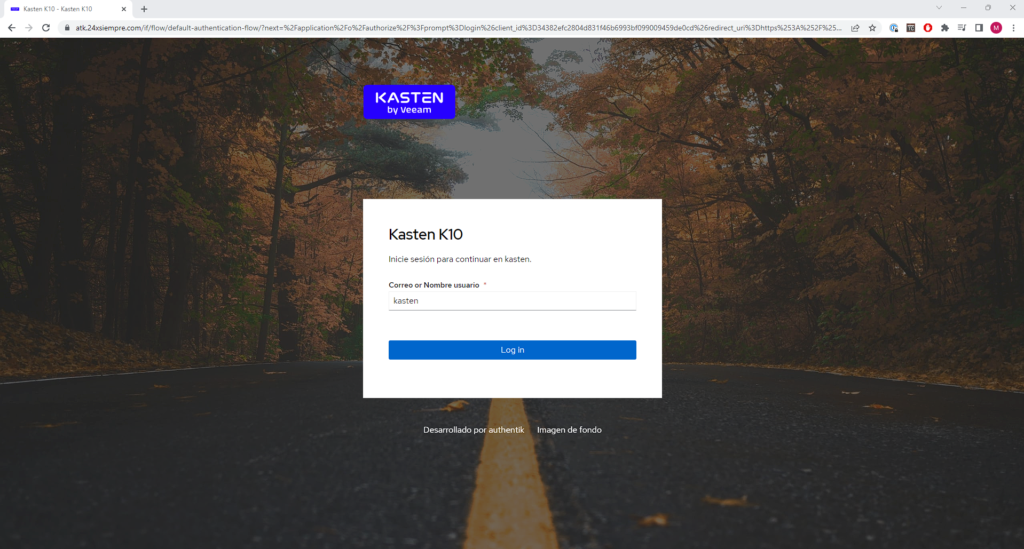
We will enter username and password
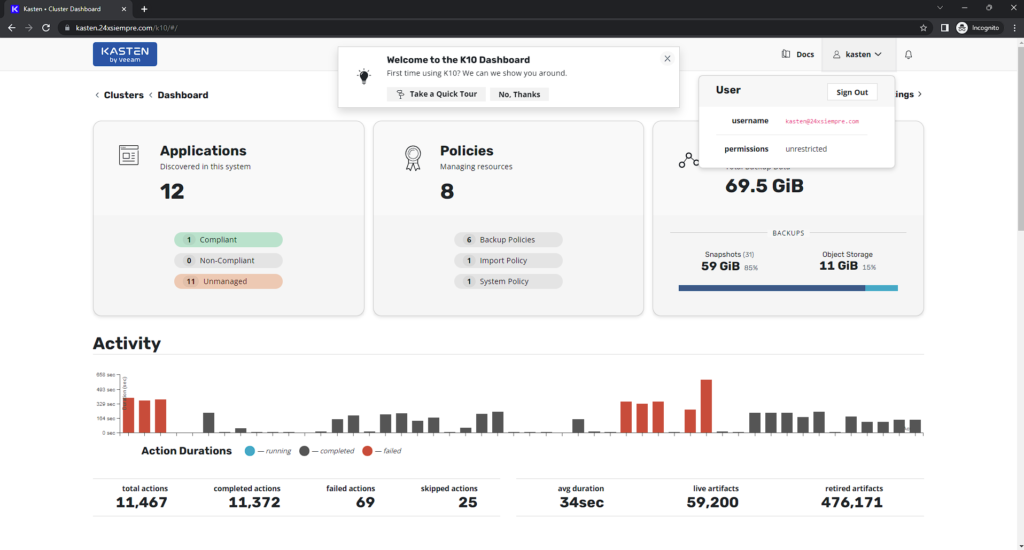
With this we finish the configuration!
