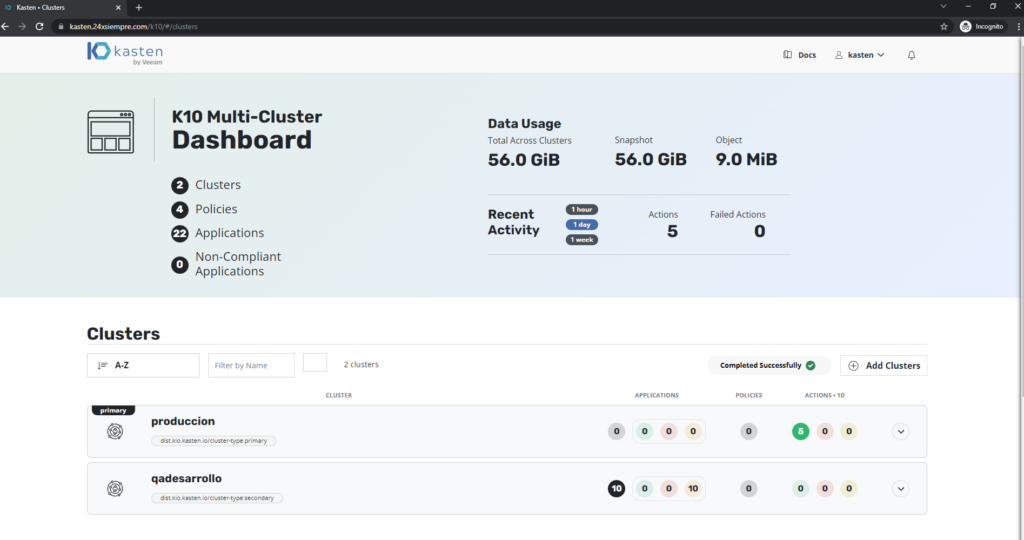
And we continue with this excellent topic that we are reviewing, in the previous post we reviewed everything related to the configuration of clusterroles, roles, bindings for Kasten K10, creating cluster roles for Administrators and for Operators of a particular cluster. In this last post we will see the configuration of roles, clusterroles, bindings with Kasten K10 Multi-Cluster Manager and of course with Keycloak for the management of Users and Groups.
Configuration Kasten K10 Multi-Cluster Keycloak
*** The idea of this series is to explain how to generate the groups, roles, clusterroles and other resources associated with RBAC, without the need to modify directly in the cluster of kubernetes user permissions over time, so all the management of user creation, groups, group assignment is done in Keycloak. ***
***OpenID configuration with Kasten K10 Multi-Cluster Manager is almost identical to that of Kasten K10, since the same steps are needed to enable Authentikation, I'll repeat them in this post, in case you landed right here.***
we should coneconnect us to the primary cluster of Kubernetes where is it installed Kasten K10 Multi-Cluster Manager and we will proceed to the Authentikation configuration with Keycloak, but first, we need to extract the “Secret” from our “Client” kasten in the “Credentials” menu replacing the variable “auth.oidcAuth.clientSecret”, (replace SuperDuperClientSecret) and of course replacing the values with your DNS or IP data, executing the following command (for security, remove part of the secret):
helm upgrade k10 kasten/k10 --namespace=kasten-io --set auth.oidcAuth.enabled=true --set auth.oidcAuth.providerURL="https://auth.24xsiempre.com/auth/realms/kasten" --set auth.oidcAuth.redirectURL="https://kast24xsiempre.com/en/" --set auth.oidcAuth.scopes="groups profile email" --set auth.oidcAuth.groupClaim="groups" --set auth.oidcAuth.prompt="login" --set auth.oidcAuth.clientID="kasten" --set auth.oidcAuth.clientSecret="SuperDuperClientSecret" --set auth.oidcAuth.usernameClaim="email" --reuse-values --set externalGateway.create=true
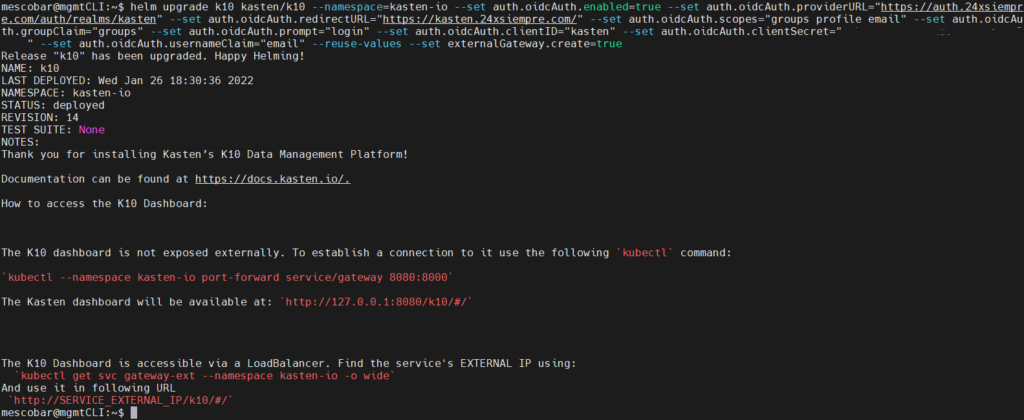
Now we will see what each of these variables means:
- --set auth.oidcAuth.enabled=true / We enable OpenID Authentikation
- –set auth.oidcAuth.providerURL=”https://auth.24xsiempre.com/auth/realms/kasten" / Url to Authenticate
- –set auth.oidcAuth.redirectURL="https://kast24xsiempre.com/en/" / application url K10
- --set auth.oidcAuth.scopes=”groups profile email” / Client Scopes to validate
- --set auth.oidcAuth.groupClaim=”groups” / Client Scope Group Name
- --set auth.oidcAuth.prompt=”login” / Login Message
- --set auth.oidcAuth.clientID=”kasten" / Name of the Client in the Realm created.
- --set auth.oidcAuth.clientSecret=”SuperDuperClientSecret” /Client secret
- --set auth.oidcAuth.usernameClaim=”email” / In case of email Authentikation
- --reuse-values / Reuse values already configured
- --set externalGateway.create=true / Reconfigure gateway service in K10 for remote access
An important piece of information if you already have an Authentikation method configured for Kasten, it is better to disable it and then run the above command on error.
Users access
As we already have everything configured, the creation of the user that we made in the previous post, we only have to enter the keycloak web interface and make sure that the user has these permissions:
- User: kastenadmin
- Password: SuperDuperPassword or the one that has been applied
- Group: k10:admins
Then we will only enter the Url of Kasten in my case https://kasten.24xsiempre. Com /k10/#/ and it will redirect us to the Keycloak login form in the realm of Kasten, we enter the credentials:
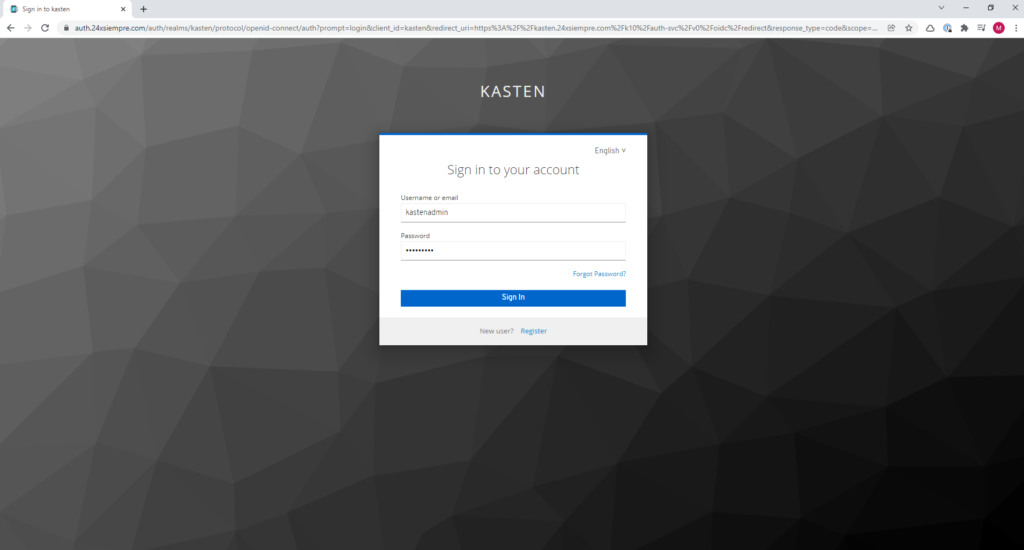
And we will be able to observe that we have a successful entry and with all the permits since we belong to the group "k10:admins” and we didn't have to edit any ClusterRole or Roles.
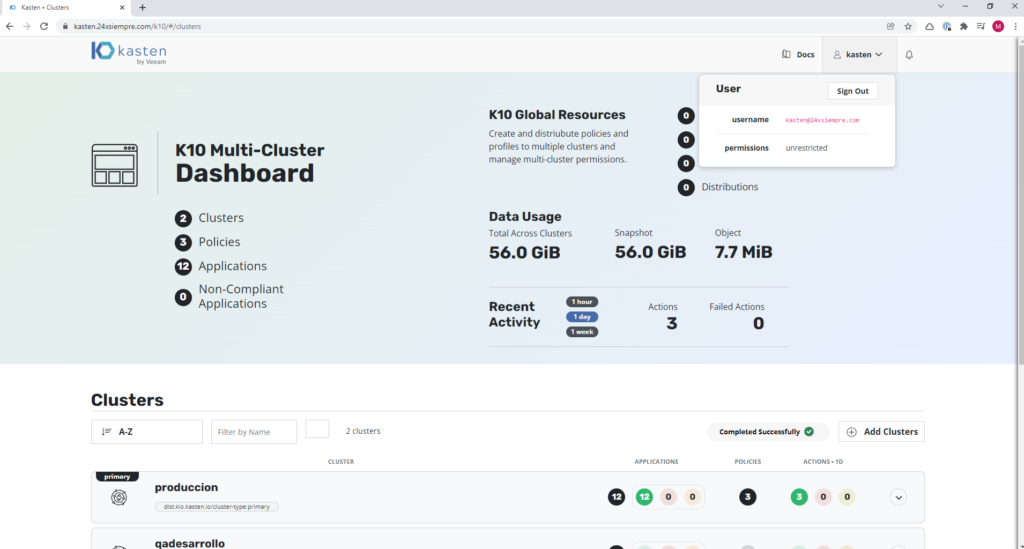
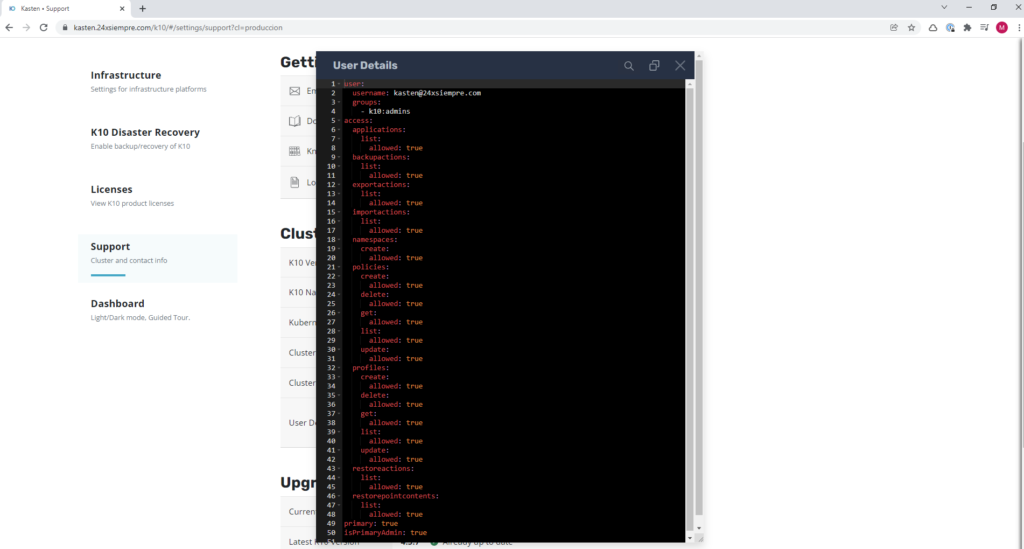
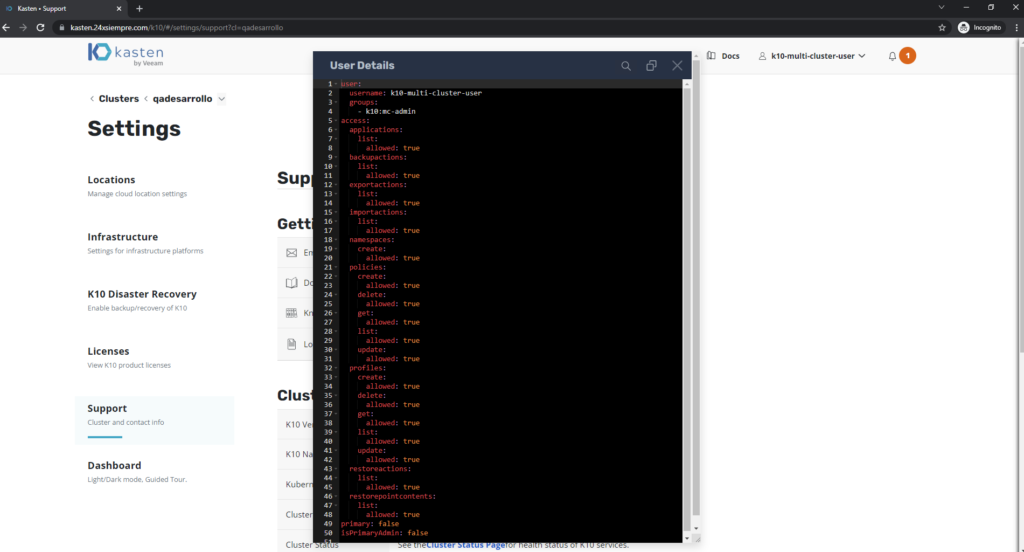
To confirm the permissions, it is possible to validate them graphically either by viewing “permissions” “unrestricted” or entering the primary cluster, then “Cluster Settings”, then “Support” and finally click on “View Current User Details” and you will be able to view all the permissions of that user and the group it belongs to:
Creation of Access Roles in Kasten K10 Multi Cluster Manager
As we saw before, we have configured the primary cluster of Kasten K10. Now we will configure the necessary roles associated with groups to access Kasten K10 Multi Cluster Manager
User Administrator
Important to note that K10 Multi-Cluster Manager is intended only for administrators, it is possible to give access to a regular user without administration permissions on Multi-Cluster Manager, even so, as we saw in the previous post, it is possible to give full access to a user to the cluster protected by K10 even if you are using resources or distributionones of Multi-Cluster Manager
By using Multi-Cluster Manager it is possible to manage users with Keycloak. as i mentionedone previously for the administration it is necessary to belong to the group “k10:admin”
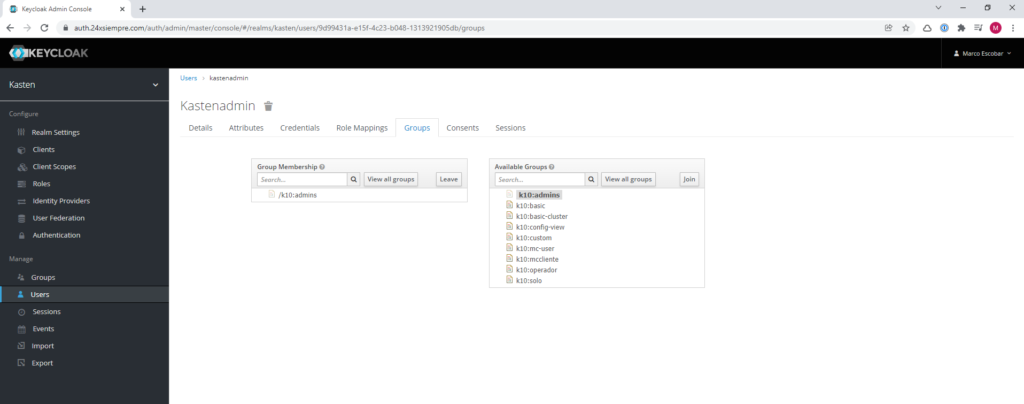
And if we validate access:
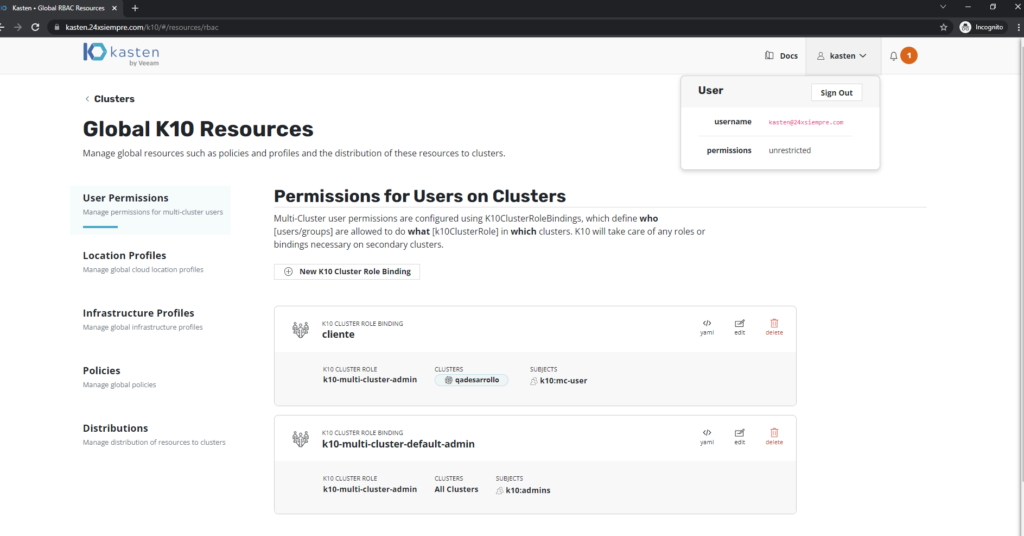
Now I need access to K10 Multi-Cluster Manager as user without the possibility to modify configurationones global.
User Operator
In general, a user with limited permissions at the user level is always necessary. K10 Multi-Cluster Manager, always remembering that it is possible to assign a direct operation role to a group of users to Kasten K10 without the need to access the Multi-Cluster Manager, therefore, in Keycloak we will change the user's group "kastenadmin” to “k10:mc-user”
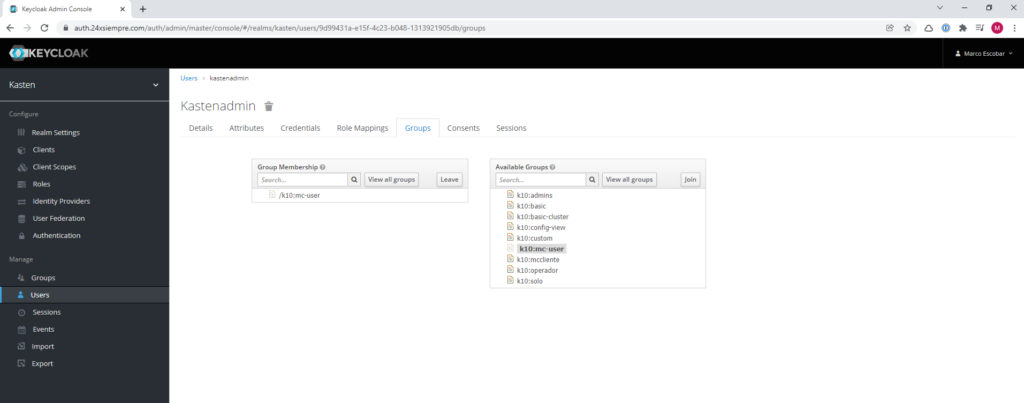
If we validate access we will get the following error:
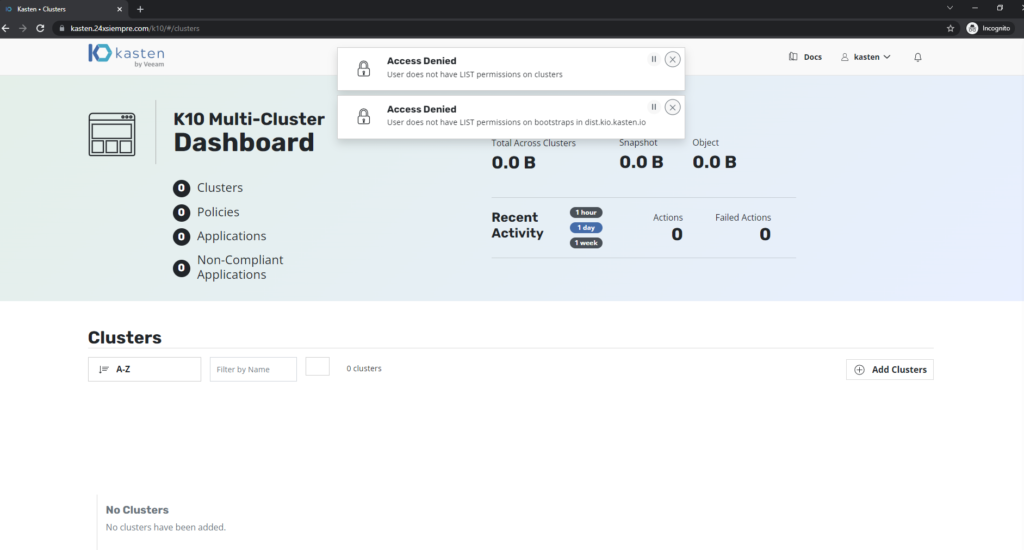
The previous error is because the RoleBinding has not been generated for the group "k10:mc-user”, so we will do it as follows:
kubectl create rolebinding k10-mc-user-demo --clusterrole=k10-mc-user \
--namespace=kasten-io-mc \
--group=k10:mc-user
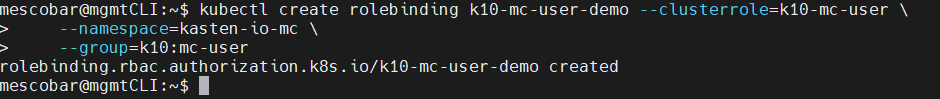
We will validate the creation of the RoleBinding:
kubectl get rolebindings -n kasten-io-mc
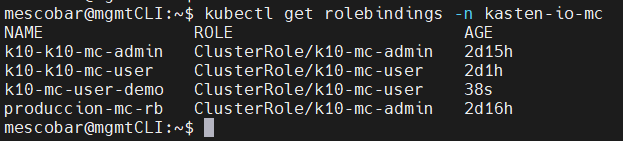
And we validate access to Kasten:
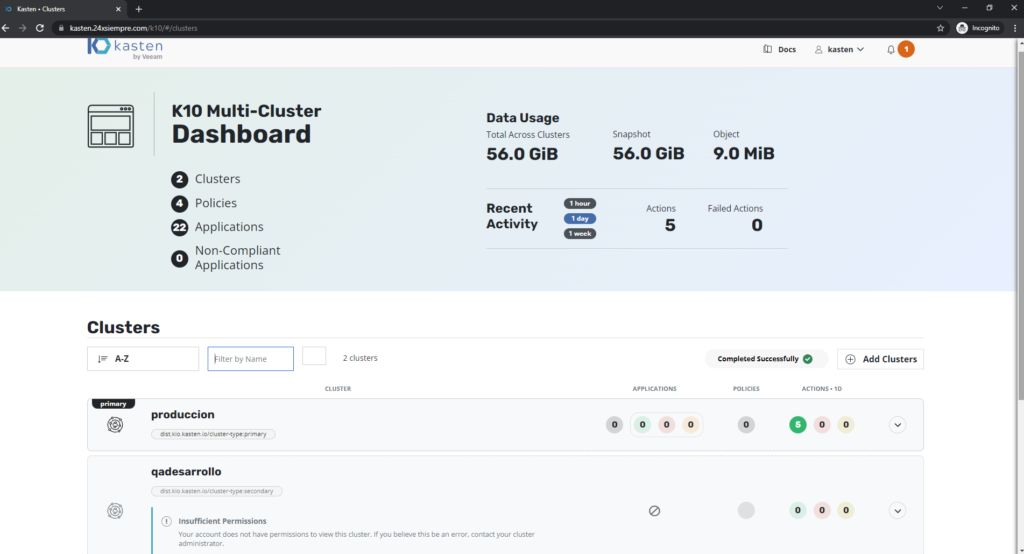
As we can see in the previous image, it does not have access to the “qadesarrollo” cluster and it cannot view the resources of the primary cluster either. It is a good practice in case of granting access to the K10 Multi-Cluster Manager, restrict the administration of the primary cluster, since the centralized configuration of all resources is concentrated in this cluster.
Assignment K10ClusterRoles in Multi-Cluster Manager
As we have already done the binding of the group at the clusterrole level, we need to allow the user access to the administration of a cluster preferably, therefore, with an administrator user, who belongs to the group “k10:admins”, we will add the user “kastenadmin” to a K10ClusterRole so that you can manage a cluster.
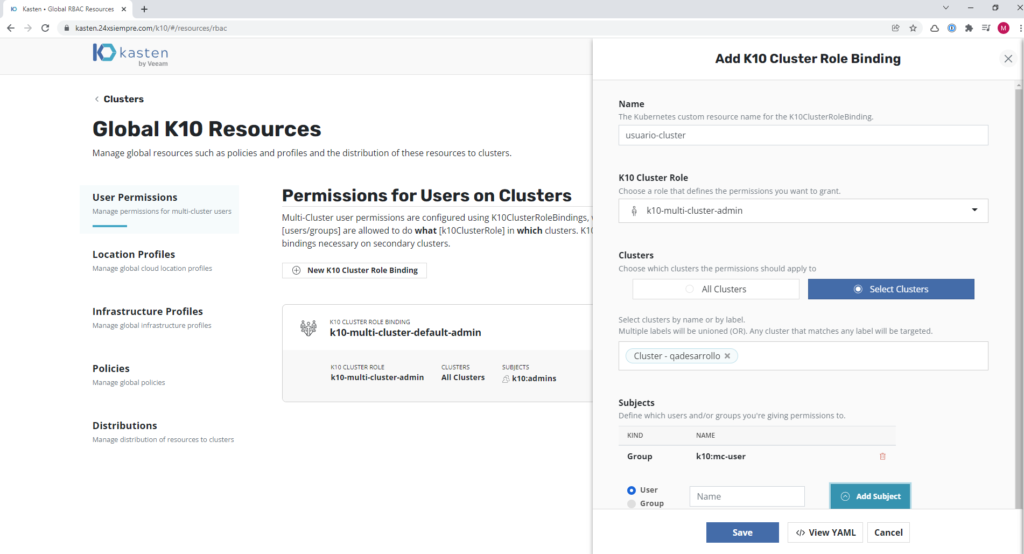
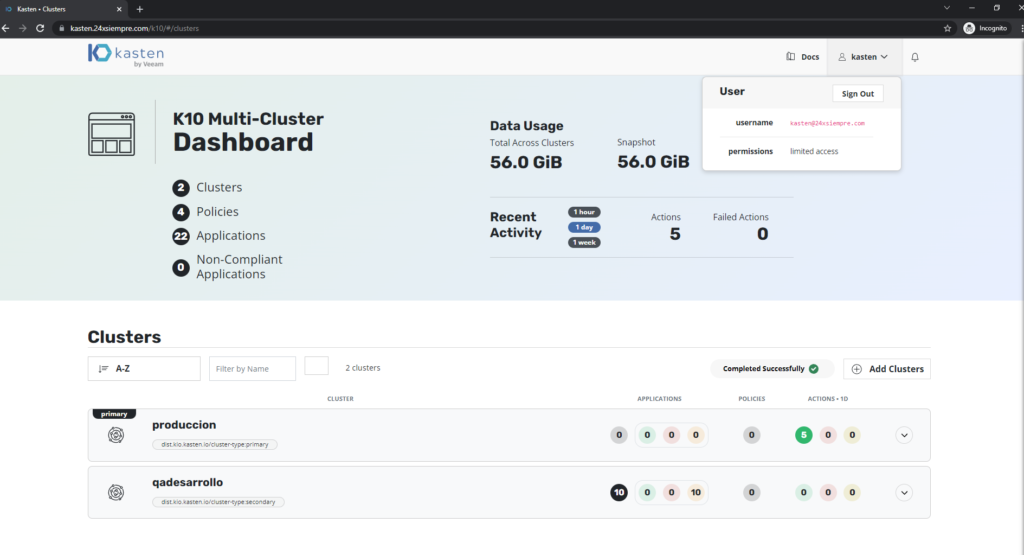
When generating the K10ClusterRole, we indicate that it is administrator of the cluster "qadesarrollo", remember that there are 3 K10ClusterRoles that you can assign to the user “k10-multi-cluster-admin”, “k10-multi-cluster-basic”, “k10-multi-cluster-config-view” and if we validate access again we will see that it already has the necessary permissions:
Conclusionones and Recommendationones
As we saw in this series of 3 posts, it is possible to use the entire RBAC to access resources with granular permissions. Kasten K10 y Kasten K10 Multi-Cluster Manager, even when clusters are managed centrally, it is possible to generate direct access to the desired cluster by any client or user of Kasten without the need to access the Multi-Cluster, it is for them that it is always recommended to use an SSO solution, as in this case Keycloak or the one of your preference since the OpenID protocol is standard. As a recommendation, always use the principle of least possible privilege and grant permissions according to the need of the operation, as well as generate the specific ClusterRoles to later only add user groups.
Book demo Kasten K10
If for any reason, you need to test this type of access, I have left the operating platform in the laboratory, so that any user can register and access the K10 Multi-Cluster Manager and be able to play with the test environment, to register and get access you just have to enter:
And click on “Register” / “Register”
When you register, it will ask for email verification and then you will have access to the laboratory. 🙂