In this post we will review the configuration of Veeam Backup & Replication and integration with Oracle KVM to protect virtual machines running on this platform. We will also see some important characteristics in relation to disks, types of disks in KVM and how to create disks to obtain Changed Block Tracking in incremental backups.
Continue reading Protecting Oracle KVM with VeeamAll articles in Security
Incident Response Plan with NIST 800-61, 800-53r5, Mitre ATT&CK and Veeam
In today's cybersecurity landscape, being prepared for incidents is as crucial as preventing them. NIST regulations 800-61 and 800-53r5, along with the Mitre ATT&CK enterprise matrix, provide solid guidelines for creating an effective incident response plan. In this post, we will review the importance of these frameworks and how the Veeam Platform it is a strategically in incident response.
Continue reading Incident Response Plan with NIST 800-61, 800-53r5, Mitre ATT&CK and VeeamWhich Operating System is More Secure?
In this post, we will review the operating systems most used by organizations in IT environments, whether in the public cloud or local data centers, asking the typical question, which operating system is more secure? Microsoft Windows, Linux, OpenBSD, FreeBSD? Or, from another point of view, what are the protection measures that will be applied to operating systems? Is only Firewall and Antivirus enough? Is it sufficient to disable the SSH service in Linux environments? Is it enough to not use root?
Continue reading Which Operating System is More Secure?How to Integrate Active Directory with Kasten K10 and OpenShift
In this post, we will review how to configure Kasten K10 installed via Operator for Red Hat Openshift to integrate the Authentikation of Microsoft Active Directory to access the console of K10 with Dex.
Continue reading How to Integrate Active Directory with Kasten K10 and OpenShiftHow to use Kasten K10 with Google Anthos
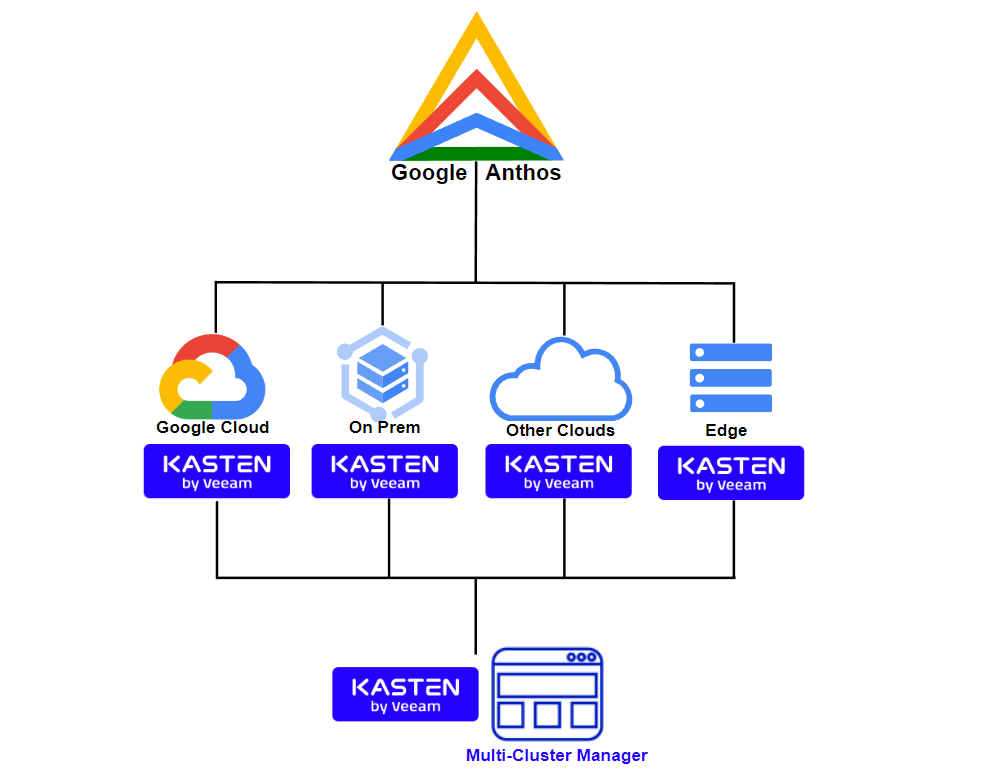
One of the architectures that are used in multiple clients with hybrid infrastructure is Google Anthos, a beautiful technology that allows to deploy clusters of Kubernetes in different environments using Google settings Kubernetes Engine, GKE, as well as adding other distributions to Google Anthos from different providers or public clouds. In this post, we will review the Anthos architecture and where to install Kasten K10 to protect applications.
Continue reading How to use Kasten K10 with Google AnthosKasten RBAC Multi-Tenant Multi-Cluster Keycloak – 1
In this post, we will look at Role Based Access Control (RBAC) configuration in conjunction with Kasten K10 for access to one or multiple clusters protected by Kasten, is aimed both at clients who manage 1 or more clusters of any distribution of kubernetes supported by K10, as well as to service providers (SP or MSP) that offer the support of containers of kubernetes with Kasten K10, with the aim of providing controlled access to users / clients according to the granular roles required by each cluster or operation. We will also use a Single Sign-On (SSO) solution using OpenID in this case, Keycloak, for the centralized management of access credentials for either users or groups.
Continue reading Kasten RBAC Multi-Tenant Multi-Cluster Keycloak – 1Veeam Immutable Repository with Red Hat Enterprise Linux
In this post, we will review installing an Immutable repository from Veeam With Red Hat Enterprise Linux, we previously reviewed an application for Ubuntu called VeeamHubRepo, which allows us to easily set up an immutable repository on Ubuntu Linux. Now we will review how to do the configuration in Red Hat Enterprise Linux, with a small script for the configuration of the repository automatically and in an easy to use way.
Continue reading Veeam Immutable Repository with Red Hat Enterprise LinuxInstall Kasten Multi Cluster Manager
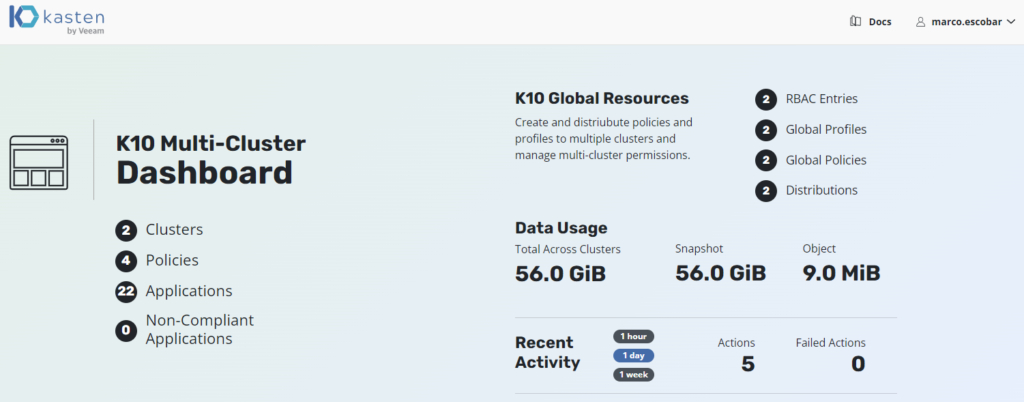
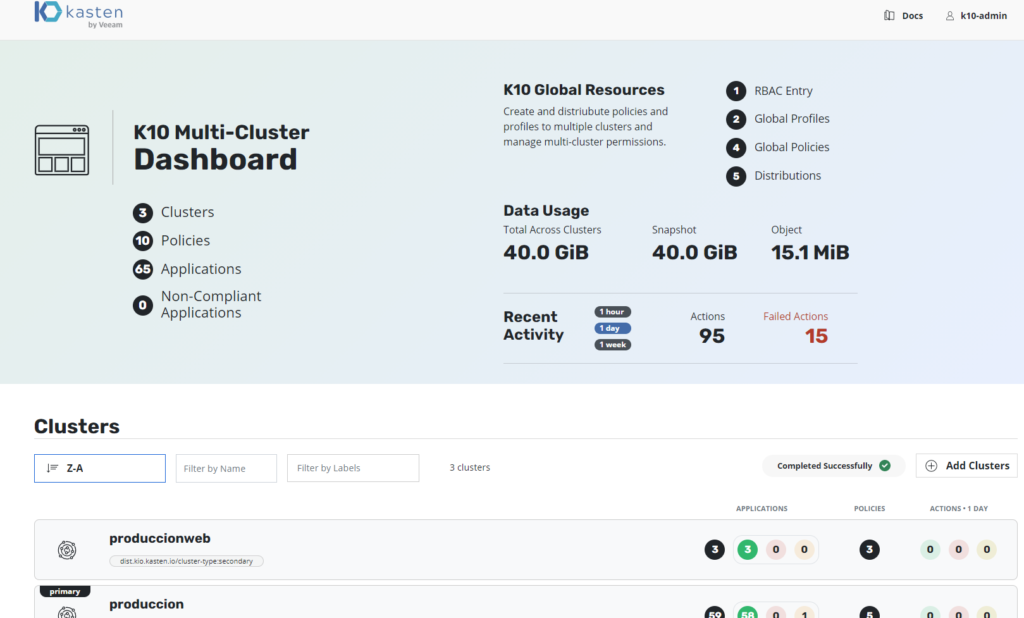
In this guide we will review how to install Kasten Multi-Cluster Manager for the management and protection of containers from multiple clusters of kubernetes in different environments with centralized resource management. Typically in most companies that maintain application development teamsones There are different types of environments such as Development, QA and Production, in other companies they also manage Pre-Production, Stagging, UAT, etc. environments. In the same way, everything depends a lot on the development life cycle as well as on the architectures of each company, which is why with Kasten Multi-Cluster Manager we will be able to achieve the protection of multiple environments and/or clusters of kubernetes.
Continue reading Install Kasten Multi Cluster ManagerVeeam Hardened (Immutable) Repository
Tremendous news with the release of version 11 of Veeam Availability Suite containing over 200 enhancements, CDP Snapshotless Replication, Instant Recovery for NAS / Databases and also Veeam Hardened Repository. In this post we will focus on the installation, configuration in detail of this new type of repository that will allow us to keep our backups immutable!
Continue reading Veeam Hardened (Immutable) RepositoryVeeam Capacity Tier Oracle Cloud Object Storage
Lately some people have asked me if Veeam supports or works with the Oracle Cloud Object Storage service, to configure it in Veeam Capacity Tier and since in the previous post we talked about Oracle, in this post we will see how to integrate the Oracle Cloud Object Storage service with a Veeam Scale-Out Backup Repository or SOBR and demonstrate the benefits of having a multi-cloud mobility solution.
Continue reading Veeam Capacity Tier Oracle Cloud Object Storage