In this post we will review the configuration of Veeam Backup & Replication and integration with Oracle KVM to protect virtual machines running on this platform. We will also see some important characteristics in relation to disks, types of disks in KVM and how to create disks to obtain Changed Block Tracking in incremental backups.
Continue reading Protecting Oracle KVM with VeeamAll articles in Red Hat
Which Operating System is More Secure?
In this post, we will review the operating systems most used by organizations in IT environments, whether in the public cloud or local data centers, asking the typical question, which operating system is more secure? Microsoft Windows, Linux, OpenBSD, FreeBSD? Or, from another point of view, what are the protection measures that will be applied to operating systems? Is only Firewall and Antivirus enough? Is it sufficient to disable the SSH service in Linux environments? Is it enough to not use root?
Continue reading Which Operating System is More Secure?How to Integrate Active Directory with Kasten K10 and OpenShift
In this post, we will review how to configure Kasten K10 installed via Operator for Red Hat Openshift to integrate the Authentikation of Microsoft Active Directory to access the console of K10 with Dex.
Continue reading How to Integrate Active Directory with Kasten K10 and OpenShiftHow to use Kasten K10 with Google Anthos
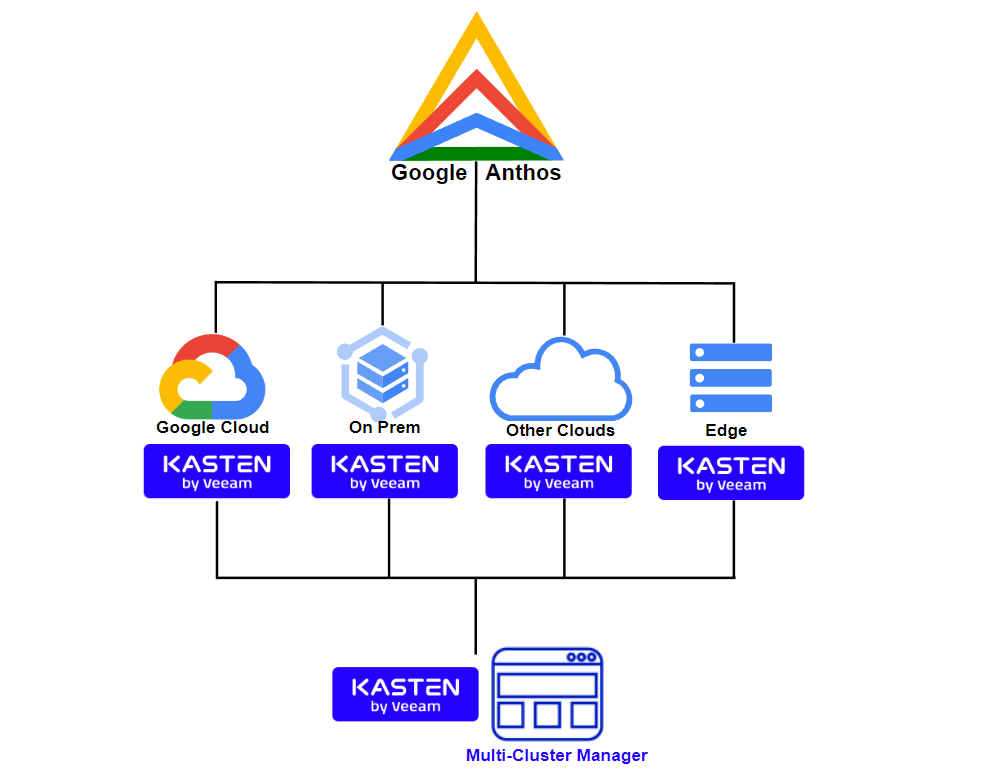
One of the architectures that are used in multiple clients with hybrid infrastructure is Google Anthos, a beautiful technology that allows to deploy clusters of Kubernetes in different environments using Google settings Kubernetes Engine, GKE, as well as adding other distributions to Google Anthos from different providers or public clouds. In this post, we will review the Anthos architecture and where to install Kasten K10 to protect applications.
Continue reading How to use Kasten K10 with Google AnthosHow to Configure NFS Repository for Kasten K10
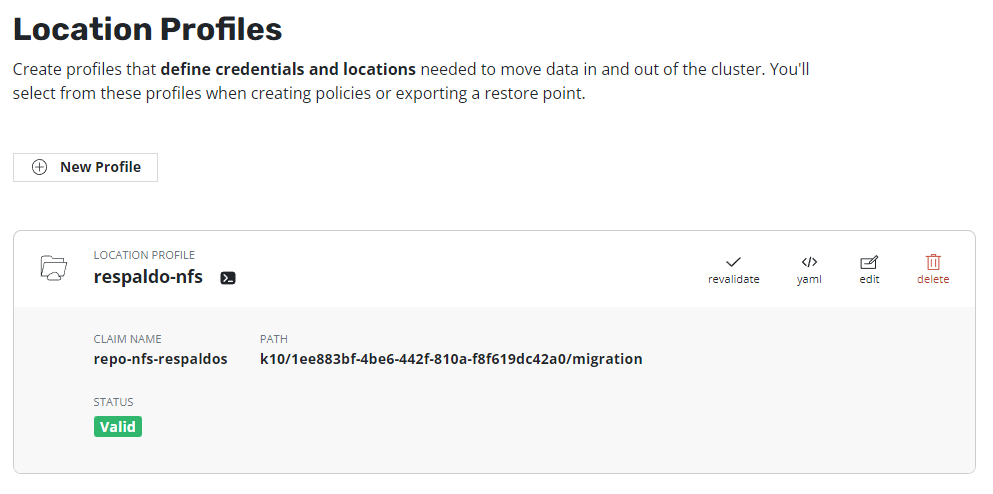
One of the options that many companies use to host their backups is NFS, in this guide, we will review how to configure an NFS Profile to be used by Kasten K10, in accordance with the good practices that are indicated in the documentation of Kasten.
Continue reading How to Configure NFS Repository for Kasten K10Kasten K10 Authentik
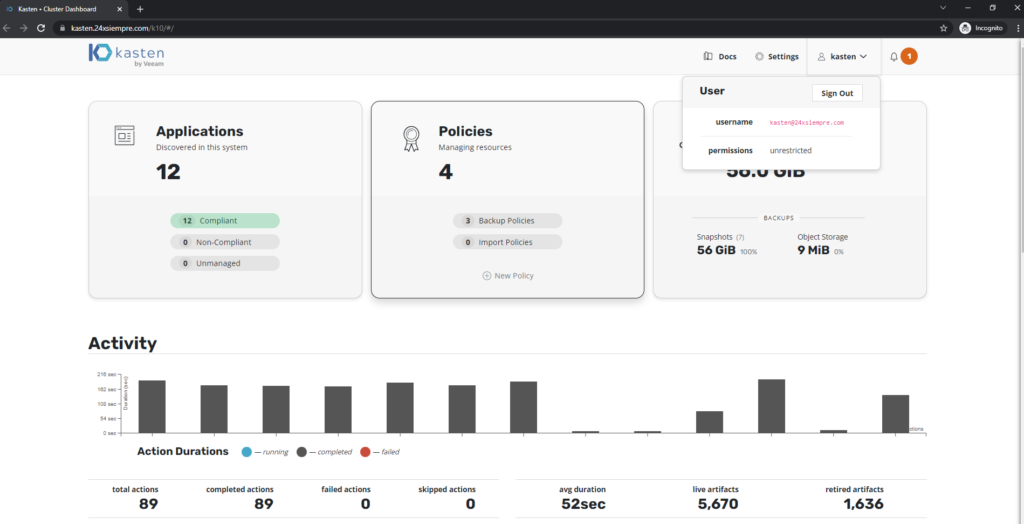
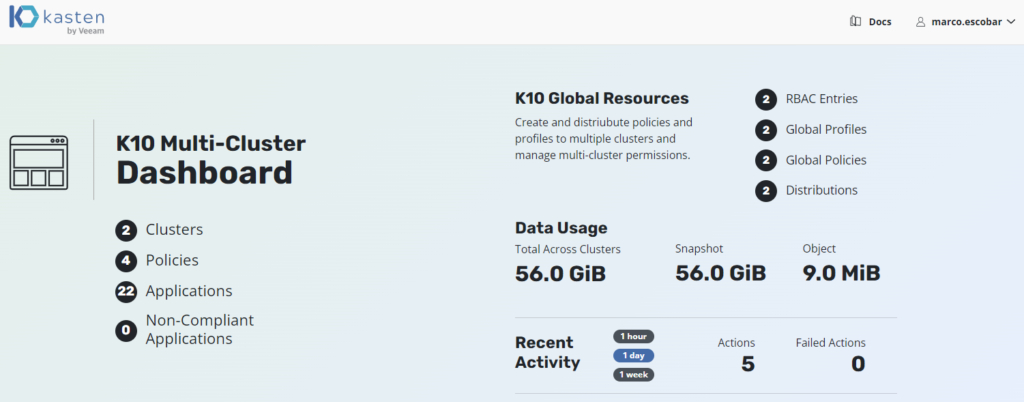
One of the characteristics of Kasten K10 most used, is the integration with centralized Authentikation and identity systems, through different protocols, for the management of access to the different clusters of kubernetes using RBAC by means of K10 and/or for the access of K10 Multi-Cluster in environments with multiple clusters of kubernetes. In this post, we will review the easy setup of Authentik and integration with Kasten K10.
Continue reading Kasten K10 AuthentikConfigure Email Alerts in Kasten K10
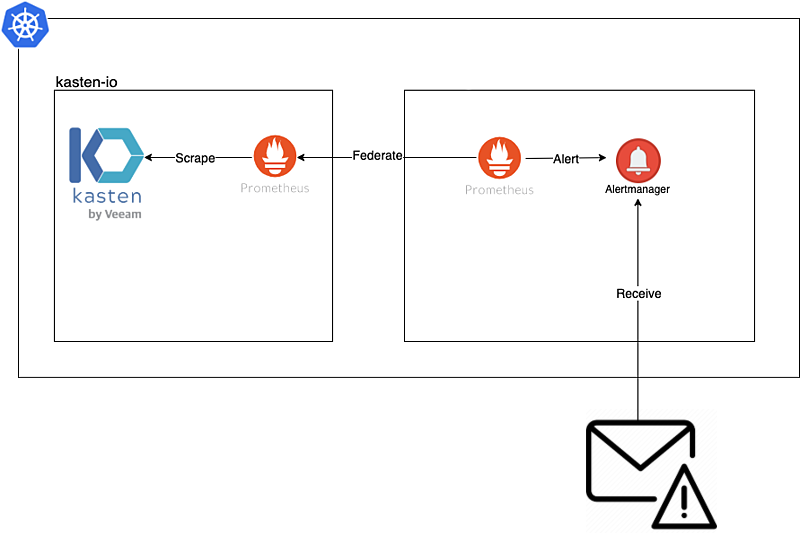
In this guide we will review the installation and configuration of prometheus in order to obtain alerts via email using the federation, rules and alertmanager of prometheus in conjunction with the monitoring of Kasten K10.
Continue reading Configure Email Alerts in Kasten K10How to Install vSphere CSI Driver on RedHat OpenShift 4.x
One of the recurring queries we have lately is how to configure the vSphere CSI Driver in environments OpenShift 4.x without the need to use the operator that VMWare already developed, but that is only supported for production from version 4.10 of OpenShift. Therefore, in this guide we will review how to install and configure the driver version.ones earlier than 4.10 without the need to use the VMware operator.
Continue reading How to Install vSphere CSI Driver on RedHat OpenShift 4.xKasten RBAC Multi-Tenant Multi-Cluster Keycloak – 2
Excellent topic we are reviewing, in the previous post we reviewed everything related to the Keycloak configuration for centralized user management through OpenID leaving it ready for integration with Kasten K10 y Kasten K10 Multi-Cluster Manager. Therefore, in this post we will see step by step the configuration of the Clusterroles, Roles and groups necessary for management via RBAC of Kasten K10.
Continue reading Kasten RBAC Multi-Tenant Multi-Cluster Keycloak – 2Kasten RBAC Multi-Tenant Multi-Cluster Keycloak – 1
In this post, we will look at Role Based Access Control (RBAC) configuration in conjunction with Kasten K10 for access to one or multiple clusters protected by Kasten, is aimed both at clients who manage 1 or more clusters of any distribution of kubernetes supported by K10, as well as to service providers (SP or MSP) that offer the support of containers of kubernetes with Kasten K10, with the aim of providing controlled access to users / clients according to the granular roles required by each cluster or operation. We will also use a Single Sign-On (SSO) solution using OpenID in this case, Keycloak, for the centralized management of access credentials for either users or groups.
Continue reading Kasten RBAC Multi-Tenant Multi-Cluster Keycloak – 1