In this post, we will review the operating systems most used by organizations in IT environments, whether in the public cloud or local data centers, asking the typical question, which operating system is more secure? Microsoft Windows, Linux, OpenBSD, FreeBSD? Or, from another point of view, what are the protection measures that will be applied to operating systems? Is only Firewall and Antivirus enough? Is it sufficient to disable the SSH service in Linux environments? Is it enough to not use root?
Continue reading Which Operating System is More Secure?All articles in Red Hat Linux
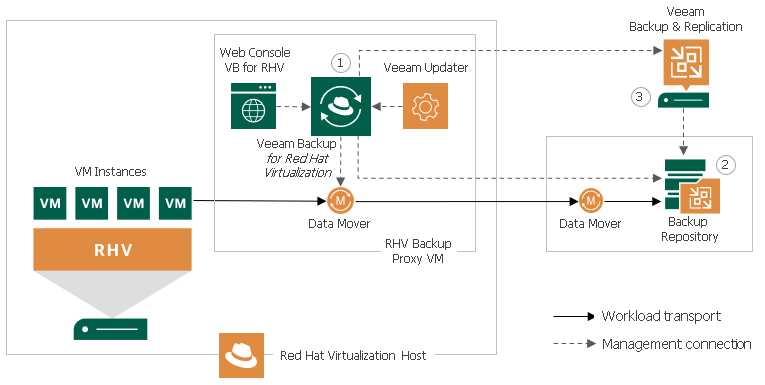
Veeam Backup for Red Hat Virtualization
tremendous news from Veeam! Now it supports a new virtualization platform, Red Hat Virtualization, with the aim of protecting virtual machines in an easy way and taking advantage of the integration of the new CBT APIs that have been implemented in RHV. In this post we will see how to deploy Veeam for Red Hat Virtualization integrated with Veeam Backup & Replication reviewing the features and dependencies necessary for complete RHV protection.
Continue reading Veeam Backup for Red Hat VirtualizationVeeam Immutable Repository with Red Hat Enterprise Linux
In this post, we will review installing an Immutable repository from Veeam With Red Hat Enterprise Linux, we previously reviewed an application for Ubuntu called VeeamHubRepo, which allows us to easily set up an immutable repository on Ubuntu Linux. Now we will review how to do the configuration in Red Hat Enterprise Linux, with a small script for the configuration of the repository automatically and in an easy to use way.
Continue reading Veeam Immutable Repository with Red Hat Enterprise Linux