In this post, we will review the operating systems most used by organizations in IT environments, whether in the public cloud or local data centers, asking the typical question, which operating system is more secure? Microsoft Windows, Linux, OpenBSD, FreeBSD? Or, from another point of view, what are the protection measures that will be applied to operating systems? Is only Firewall and Antivirus enough? Is it sufficient to disable the SSH service in Linux environments? Is it enough to not use root?
Introduction
Some time ago, and in recent VeeamON Tours of Latin America, I talked with clients and co-workers about the typical question: Which operating system is more secure? Some said Linux is always safer, others said Windows, and finally, others opted for OpenBSD (One of its objectives is to be the most secure OS) and FreeBSD, but the operating system really matters, or what matters is the way it is deployed. And are operating systems protected? Always speaking from a security point of view.
In general, there is always talk of “hardening” operating systems, aiming for default security, but is this “hardening” updated over time? People who indicate that Linux is more secure, how many times do they update Linux servers since a vulnerability is found? In general, in Latam and according to my experience, there are very few organizations I know yes. They keep their servers with the Linux or BSD operating system up to date. Still, another no small part prefers to be exposed to any attack based on a Linux/BSD vulnerability or an application that provides services. And not to mention the professionals who do not want to update Windows because they do not know if the solution they have installed will work or they have the idea that "they are not going to attack my company."
Is your Organization prepared to receive an Attack?
It is a tremendous question since it is not easy to answer, and in general, the answer is always No since there can be many factors in organizations that do not allow IT areas to minimize the risk, for example, some of the most common problems I have seen:
- Budget
- Old or Legacy Applications
- Lack of training
- Lack of use of a Security Framework
- Lack of Controls in IT Infrastructure
- Credential Reuse
- Lack of use of RBAC or Role based Access Control
- Lack of documentation
So, with the previous examples, it becomes very complex to prepare for an attack, in fact, it is only necessary to do some type of OSINT to identify specific organizations with their respective published services (RDP, ILO, SQL, IDRAC, etc.) on the Internet without the necessary security.
What Security Framework to use to minimize the Risk?
As additional information, since when talking about security frameworks a separate post is necessary, the first framework to use in your organization may be the Cyber Security Framework(CSF) either the currently published version 1.1 or the next one that is in a draft, 2.0, from the National Institute of Standards and Technologies of the USA ( NIST), where, according to version 2.0, are six main functions:
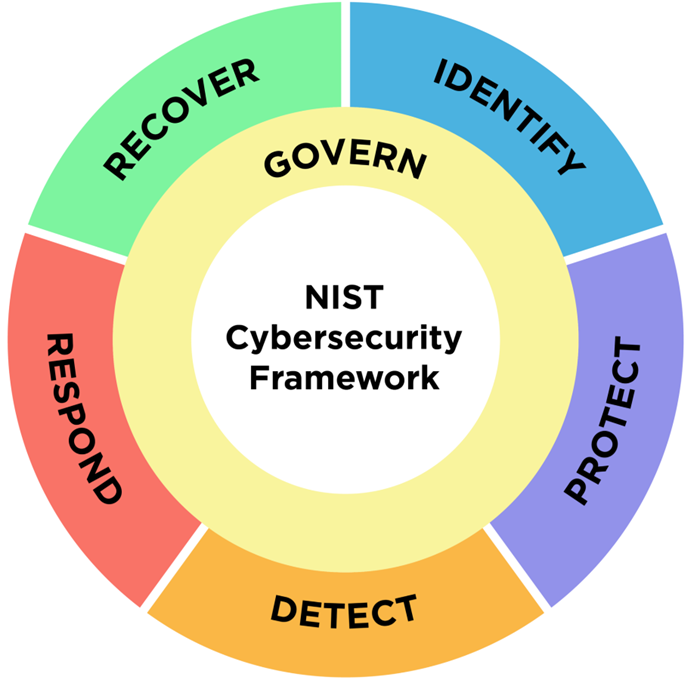
With these functions, it is possible to implement a necessary strategy to minimize the cybersecurity risk so that in the event of an attack, you can react promptly. An excellent recommendation in conjunction with CSF is the use of the special publication SP 800-53r5 for the application of the necessary controls.
- CSF https://www.nist.gov/cyberframework
- SP 800-53r5 https://csrc.nist.gov/pubs/sp/800/53/r5/upd1/final
What Operating System to choose for the Services to be Provided?
Returning to the main topic, Which Operating System is More Secure?, the first thing we must review is which service or services we are going to install or use on our server; then, depending on the organization or manufacturer's requirements, check if the implementation of The solution may be possible in the native cloud, hybrid, on-premises, Kubernetes, serverless to find the best way to provide high availability.
Now, regarding the decision with which operating system to work, whether defined by the software that will run on the server or by organizational guidelines, the first thing we must review is if we are going to expose services to the Internet, what type of services, Authentikation of internal or external users, to achieve what will be the security solutions that will allow us to provide at least basic protection to deliver the services.
Already having knowledge of the services to be provided, it is necessary to define ALWAYS, what will be the protection of these services or operating system, of course, with a correct data backup strategy, which allows us to recover the data in different ways so that in case of attack, we have multiple options recoveries according to the need for business continuity.
Finally, by reviewing the requirements of the software or platform to be installed on the server, a decision can be made that is favorable for the solution and is directly related to the security policies of the organization or company.
So, Which Operating System is More Secure?
The answer is quite simple: the most secure operating system will always be the one that complies with a correct implementation from a point of view of comprehensive security and safe use, complying with security controls, for example 800-53r5, application of local security policies, monitoring, use of different network and local security systems, therefore, it is not only about the operating system, it is about all the procedures, tools, security policies that accompany the management and use of the services to be used.
All operating systems, including applications, have or will have security vulnerabilities since there will always be people or organizations dedicated to finding some type of vulnerability, whether as a hobby, malware creation, or a beautiful research.
Therefore, one of the options the best thing to always consider is to review the capacity or frequency of security updates or features of the different manufacturers of operating systems and applications; for example, in the case of some solutions based on Kubernetes, the update frequency of the images used and the application as such, are continually improved or updated to minimize the risk of any vulnerability.
That is why it is not an issue of the operating system type; for example, is Linux more secure than Windows? Windows is more secure than Linux? is MacOS more secure than the previous ones? OpenBSD, is it the most secure system? As we have seen, none is safer than the other since it is only necessary to search the different Vulnerabilities databases:
In the previous links, you will find not only the vulnerabilities of the operating systems but also of the applications that can run on servers or workstations.
Monitoring and Protection
Every time a new server is generated, whether virtual or physical, SHOULD, have an associated mechanism for monitoring services and behavior of the different resources that the server will be using and MANDATORY the patch update scheme and data protection, of course with Veeam :), since as we saw previously when using a security framework, it is imperative to have the information on what the disaster recovery plans will be and the definition of RTO / RPOto meet the necessary times.
Why is Monitoring important? Beyond monitoring services, current monitoring systems, such as Veeam ONE, allow you to have information on the behavior of the virtual machines; that is, it is possible to identify the consumption of IOps, CPU, which could be suspicious on a day that is not a monthly load, with this, by having the necessary information it will be possible to apply the corrective actions manually or automatically.
For example, for zero-day or 0-day vulnerabilities, it is of utmost importance to monitor the systems or services to know if these vulnerabilities are being exploited or if the server has started exhibiting abnormal behavior.
Updates
Yes or yes, maintain strict update policies, independent of the operating system used, since the first attack is to take advantage of existing vulnerabilities in operating systems, for example, remote command execution, RCE, which has recently been used in versions of VMware hypervisors. On the other hand, by having the operating systems updated, it is also of utmost importance to keep the dependencies and applications updated that will be providing services, such as solutions of Atlassian, that multiple critical vulnerabilities have been found lately.
Security Application Technical Guides
One of the widely used practices is the application of guides DISA STIG, OpenSCAP, whether for operating systems or for applications that will be executed on the servers. It is crucial to review these guides since the recommendations could be fully implemented select the recommendations that indicate, for example, if you need to apply security controls for Microsoft Windows Server 2022 and Ubuntu 20.04, you only have to visit:
To mention a few, there are more; depending on the need, it will be possible to apply the necessary controls according to the need or business of your organization.
Bad Security Practices in Operating Systems or Services
Some that I have seen repeatedly:
- Use Administrator or root to install applications
- Use the same access credentials by multiple users Ex: [email protected]
- Do not use or enable MFA
- Not having a strict password change and complexity policy.
- Not having a backup and recovery testing policy.
- Do not centralize logs or events of operating systems and applications
- Save passwords to an Excel/TXT file
- Little or no documentation of systems or architectures.
- Using only Antivirus
- No use of encryption
Good Security Practices in Operating Systems or Services
Some that should be used:
- Always use service accounts for applications
- Segment and apply RBAc to accounts by user
- Disable default or unused accounts
- Enable MFA where possible and save backup codes.
- Apply Password Change Policy
- Back up all data where possible and test recovery from time to time
- Monitor and save logs of all critical systems
- Use Business Password Managers
- Document all necessary architectures and processes.
- Use of security solutions in each of the operating systems
- Encrypt communications and Backups
Recommendations
The first mandatory rule is always to keep all operating systems and services installed on the server updated, in addition to the corresponding monitoring either from the point of view of service availability or audit logs to identify strange behavior to the solution and apply corrective measures.
Of course, install solutions in the different operating systems (not just Windows) to obtain a complete vision and monitoring from a security point of view.
Always use the principle of least privilege and do not use weak Authentication methods; if the service is not being used, disable it or simply uninstall the service completely.
And, of course, the use of the Platform Veeam to protect all your data in the organization, whether in your data center, Public Cloud, or workstations, validating recoverability in an automated way, analyzing and searching for malware in backups and then automatically creating and documenting Disaster Recovery Plans, DRP, to recover the organization with the data in a clean and accessible manner without reinfection.
